Secure Payment Confirmation, Stripe Experiment, and Next Steps
On 18 March Stripe presented the results of their 3-month experiment with Secure Payment Confirmation (SPC) to the Web Payments Working Group (minutes). The results were quite exciting: conversions went up by 8% and authentication sped up considerably. I share details below and you can find more in the Stripe presentation.
The vision for SPC is to streamline strong customer authentication (SCA) during a Web payment. This will improve Web commerce experiences, enhance security, and help the payments industry fulfill regulatory requirements (e.g., PSD2 in Europe). SPC does not yet exist as an API or a well-defined set of browser behaviors. The Stripe experiment tested some hypotheses for what SPC could become. Google engineers made the experiment possible through modifications to implementations of Web Authentication and Payment Request API in Chrome on MacOS. The Web Payments Working Group is about to embark on a more systematic elaboration of SPC's features and scope.
The Stripe experiment sought to understand if users prefer strong authentication through one-time passwords or FIDO authentication. Why FIDO? The combination of CTAP from the FIDO Alliance and Web Authentication from W3C —commonly referred to as FIDO2— is an ideal backbone for an SCA solution. It is supported on all major browsers (desktop and mobile). Billions of deployed phones and laptops include built-in authenticators. FIDO2 provides better security and usability than passwords and explicitly seeks to meet regulatory requirements (see the FIDO white paper on meeting PSD2 SCA requirements).
For simplicity, the SPC experiment focused on card payments where the initial enrollment was performed with EMV® 3-D Secure ("3DS"). As I mentioned in a previous blog post, EMVCo, FIDO, and W3C are discussing multiple ways of using FIDO with 3DS. The experiment focused on using FIDO during the 3DS challenge flow. This proved a very informative starting point, but part of our ongoing work will be to ensure that SPC can be used in a broad range of payment flows and systems.
To understand the motivation for SPC, it is useful to consider how 3DS works on the Web today. My explanation is a simplified version.
- An important design goal 3DS is to enable the bank that issues a credit card to determine whether the person planning to use the card for an ecommerce payment is authorized to do. However, when a user is shopping, the user is interacting with a merchant, not their bank.
- One way to "get the user to the bank" is through an HTTP redirect to the bank's Web site (in a first party context) for authentication. People tend to not like this solution for a variety of usability reasons. Merchants do not like directing their customers away from their site.
- Another solution is to include code from the issuing bank in the merchant site (in a third party context). Payment services providers (to merchants) typically take this approach using iframes, but without Web Authentication.
Let's examine why. In Web Authentication Level 1:
- A relying party must register an authenticator in a first party context.
- The relying party is the only party that can authenticate the user.
- The relying party can only do so in a first party context.
In other words, with Web Authentication Level 1, the issuing bank (assuming it operates in a different origin than the merchant) could not use Web Authentication to authenticate the user within the merchant page (in a third party context).
To overcome this limitation, the Web Payments Working Group asked the Web Authentication Working Group for an enhancement. As a result, in Web Authentication Level 2:
- A relying party must register an authenticator in a first party context.
- The relying party is the only party that can authenticate the user.
- The relying party can do so in either a first or third party context.
Now the issuing bank can authenticate the user with Web Authentication from within a merchant page. That's already a big win. But Stripe sought further improvements. They pointed out that embedding code from an issuing bank in a page involves more network calls and could create security policy issues. Instead, they wanted to be able to trigger Web Authentication themselves, collect the resulting assertion, and pass that on to the issuing bank through back channels. The issuing bank would still validate the assertion as the relying party.
This is how the first "superpower" of SPC came about. With SPC:
- A relying party must register an authenticator in a first party context.
- Any party can authenticate the user.
- Any party can do so in either a first or third party context.
This is an important departure from Web Authentication behavior and so it is only available "in a payments context." The current (experimental) definition of "in a payments context" is "during Payment Request API."
SPC, in its pilot manifestation, thus marries Payment Request API and Web Authentication. The idea is that developers will have more superpowers via SPC than when the APIs are used independently.
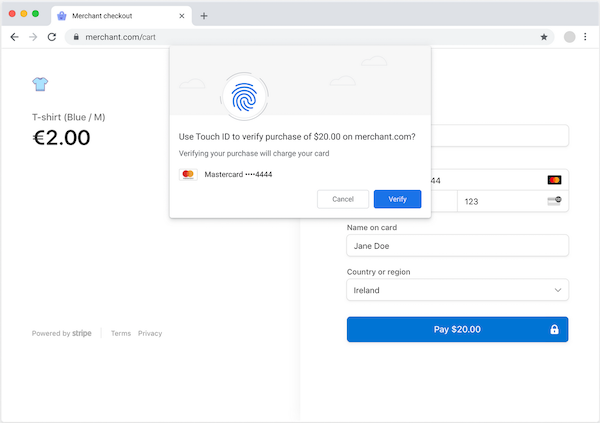
The second superpower of SPC is the browser's "transaction confirmation dialog." The goal is to have a built-in browser capability to create a consistent authentication experience across Web sites and platforms.
This is another departure from Web Authentication. Web Authentication is performed within a window opened by some origin. Stripe asked the Chrome team if the browser could manage the window instead of Stripe having to open one. The result is a built-in browser dialog, shown in the mockup included above. SPC delegates the authentication UX to the browser. Here's how SPC worked during the experiment, leading up to the transaction confirmation dialog:
- During an enrollment (which I won't describe in detail here), the user registers an authenticator with the issuing bank in a first party context. The issuing bank associates the user's card with that FIDO credential.
- During a transaction, on any merchant site, the user selects the same card to make a payment. Stripe (or any PSP) reaches out to the issuing bank (via a modified 3DS protocol) and asks: Do you have any FIDO credentials associated with this card? The issuing bank returns the shareable parts of any credentials it has stored, along with a random number (which will be used during authentication). Stripe calls SPC, and the browser opens the transaction confirmation dialog, asking the user: "Do you want to authenticate to pay N dollars to the following merchant using this card?" If the user proceeds, the platform (in this case MacOS) prompts the user to authenticate (in the experiment, using TouchID).
Stripe also wanted to leverage SPC to fulfill another PSD2 requirement: "dynamic linking." The requirement involves cryptographic evidence that the user agreed to the transaction amount and beneficiary. The browser's new transaction confirmation dialog displays the information required by PSD2, and when the user proceeds, the FIDO authenticator is used to sign the amount, beneficiary, and card information. Thus, the third superpower of SPC is built-in support for signed transaction confirmation data.
To summarize, the initial experiment with SPC involved these three new browser capabilities:
- Relaxation of the constraint on who can authenticate the user for a given FIDO credential during Payment Request API
- Transaction confirmation dialog built into the browser
- Signed transaction data
We have started work to elaborate a list of SPC benefits that emerge from these three capabilities. I imagine these initial three capabilities will remain part of the SPC vision, but people are already curious whether we can add more, such as standardized enrollment flows, zero-friction flows, sources of randomness as input to FIDO authentication, and the ability to invoke SPC within a Payment App. We will discuss potential SPC features at the remote meeting of the Web Payments Working Group next week.
Back to the experiment. How did SPC compare to one-time passwords? Stripe shared with us that with SPC:
- Conversions (completed transactions) increased 8%.
- Users authenticated in less than 1/3 of the time.
- There was negligible fraud.
I expect the Working Group will want to take up SPC as a formal work item, which means we'll have a lot to do:
- More experimentation (including with banks)
- Initial work on a specification.
- Expansion of implementation by Google to other platforms.
- Engagement with more browser vendors.
- Discussion of requirements from a variety of payment systems and flows (e.g., EMV® Secure Remote Commerce ("SRC"), Real-Time Payments from The Clearing House, Open Banking in Europe, etc.)
- Coordination with the Web Authentication Working Group and the FIDO Alliance to make sure that SPC aligns with that work.
- Coordination with the EMVCo 3DS Working Group for any enhancements to 3DS or SRC to support SPC.
- Understanding how SPC relates to other authentication delegation use cases; see for instance the new white paper FIDO for SCA Delegation to Merchants or Wallet Providers. The Web Payment Security Interest Group provides EMVCo, FIDO, and W3C the forum for discussing these use cases and how to make sure the various technologies can interoperate flexibly.
I want to thank all the people who have contributed to discussions, coding, and experimentation so far, especially colleagues at Stripe, Google, and Coil.
EMV® is a registered trademark in the U.S. and other countries and an unregistered trademark elsewhere. The EMV trademark is owned by EMVCo, LLC.
Will FIDO replace the need of 3DS native mobile SDK ? as authentication could be done on browser flow more securely with FIDO. Will the merchants still look for a native solution such as a 3DS Mobile SDK ?
Hello,
As mentioned in the previous blog post [1] the community is looking at a variety of ways to leverage FIDO within 3DS flows. I expect there will be a variety of use cases (e.g., logged in users, guest checkout, large v. small merchants, different regulatory requirements, etc.) that we will see a variety of applications.
Ian
[1] https://www.w3.org/blog/wpwg/2021/02/18/an-emv-3-d-secure-view-of-emvco-fido-and-w3c-activities/