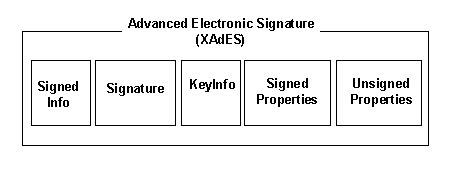
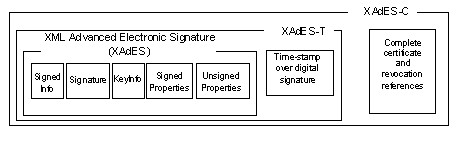
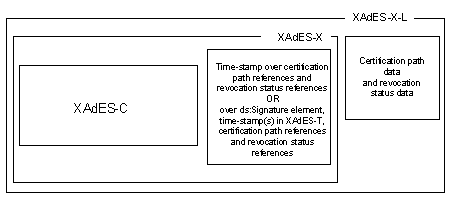
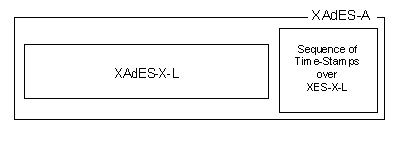
<?xml version="1.0" encoding="UTF-8"?>
<!ENTITY % Any.ANY ''>
<!ENTITY % XMLTimeStamp.ANY ''>
<!-- Start Any -->
<!ELEMENT Any (#PCDATA %Any.ANY;)*>
<!-- End Any -->
<!-- Start ObjectIdentifier -->
<!ELEMENT ObjectIdentifier (Identifier, Description?, DocumentationReferences?)>
<!ELEMENT Identifier (#PCDATA)>
<!ATTLIST Identifier
Qualifier (OIDAsURI | OIDAsURN) #IMPLIED
>
<!ELEMENT Description (#PCDATA)>
<!ELEMENT DocumentationReferences (DocumentationReference)+>
<!ELEMENT DocumentationReference (#PCDATA)>
<!-- End ObjectIdentifier -->
<!-- Start EncapsulatedPKIData -->
<!ELEMENT EncapsulatedPKIData (#PCDATA)>
<!ATTLIST EncapsulatedPKIData
Id ID #IMPLIED
>
<!-- End EncapsulatedPKIData -->
<!-- Start EncapsulatedTimeStamp -->
<!ELEMENT TimeStamp (HashDataInfo+, (EncapsulatedTimeStamp | XMLTimeStamp))>
<!ELEMENT HashDataInfo (Transforms?)>
<!ATTLIST HashDataInfo
uri CDATA #REQUIRED
>
<!ELEMENT EncapsulatedTimeStamp (#PCDATA)>
<!ATTLIST EncapsulatedTimeStamp
Id ID #IMPLIED
>
<!ELEMENT XMLTimeStamp (#PCDATA %XMLTimeStamp.ANY;)*>
<!-- End EncapsulatedTimeStamp -->
<!-- Start container types -->
<!-- Start QualifyingProperties -->
<!ELEMENT QualifyingProperties (SignedProperties, UnsignedProperties?)>
<!ATTLIST QualifyingProperties
Target CDATA #REQUIRED
Id ID #IMPLIED
>
<!ELEMENT SignedProperties (SignedSignatureProperties, SignedDataObjectProperties?)>
<!ATTLIST SignedProperties
Id ID #IMPLIED
>
<!ELEMENT UnsignedProperties (UnsignedSignatureProperties?, UnsignedDataObjectProperties?)>
<!ATTLIST UnsignedProperties
Id ID #IMPLIED
>
<!-- End QualifyingProperties -->
<!-- Start SignedSignatureProperties, SignedDataObjectProperties,
UnsignedSignatureProperties, UnsignedDataObjectProperties -->
<!ELEMENT SignedSignatureProperties (SigningTime, SigningCertificate,
SignaturePolicyIdentifier, SignatureProductionPlace?, SignerRole?)
>
<!ELEMENT SignedDataObjectProperties (DataObjectFormat*, CommitmentTypeIndication*,
AllDataObjectsTimeStamp*, IndividualDataObjectsTimeStamp*)
>
<!ELEMENT UnsignedSignatureProperties (CounterSignature*, SignatureTimeStamp*,
CompleteCertificateRefs?, CompleteRevocationRefs?,
(SigAndRefsTimeStamp* | RefsOnlyTimeStamp*), CertificateValues?,
RevocationValues?, ArchiveTimeStamp*)
>
<!ELEMENT UnsignedDataObjectProperties (UnsignedDataObjectProperty*)>
<!ELEMENT UnsignedDataObjectProperty (#PCDATA %Any.ANY; )*>
<!-- End SignedSignatureProperties, SignedDataObjectProperties,
UnsignedSignatureProperties, UnsignedDataObjectProperties -->
<!-- Start QualifyingPropertiesReference -->
<!ELEMENT QualifyingPropertiesReference (Transforms?)>
<!ATTLIST QualifyingPropertiesReference
URI CDATA #REQUIRED
Id ID #IMPLIED
>
<!-- End QualifyingPropertiesReference -->
<!-- End container types -->
<!-- Start SigningTime -->
<!ELEMENT SigningTime (#PCDATA)>
<!-- End SigningTime -->
<!-- Start SigningCertificate -->
<!ELEMENT SigningCertificate (Cert+)>
<!ELEMENT Cert (CertDigest, IssuerSerial)>
<!ELEMENT CertDigest (DigestMethod, DigestValue)>
<!ELEMENT IssuerSerial (X509IssuerName, X509SerialNumber)>
<!-- End SigningCertificate -->
<!-- Start SignaturePolicyIdentifier -->
<!ELEMENT SignaturePolicyIdentifier (SignaturePolicyId | SignaturePolicyImplied)>
<!ELEMENT SignaturePolicyId (SigPolicyId, Transforms?, SigPolicyHash, SigPolicyQualifiers?)>
<!ELEMENT SignaturePolicyImplied ANY>
<!ELEMENT SigPolicyId (Identifier, Description?, DocumentationReferences?)>
<!ELEMENT SigPolicyHash (DigestMethod, DigestValue)>
<!ELEMENT SigPolicyQualifiers (SigPolicyQualifier+)>
<!ELEMENT SigPolicyQualifier (#PCDATA %Any.ANY; )*>
<!-- End SignaturePolicyIdentifier -->
<!-- Start SPURI and SPUserNotice -->
<!ELEMENT SPURI (#PCDATA)>
<!ELEMENT SPUserNotice (NoticeRef?, ExplicitText?)>
<!ELEMENT NoticeRef (Organization, NoticeNumbers)>
<!ELEMENT ExplicitText (#PCDATA)>
<!ELEMENT Organization (#PCDATA)>
<!ELEMENT NoticeNumbers (#PCDATA)*>
<!-- End SPURI and SPUserNotice -->
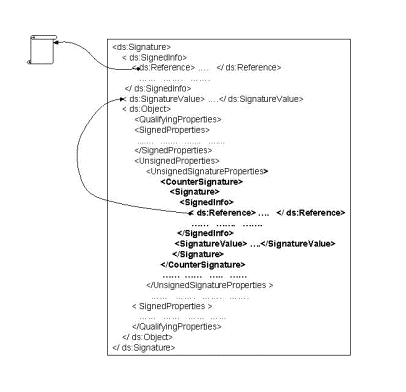
<!-- Start CounterSignature -->
<!ELEMENT CounterSignature (Signature)>
<!-- End CounterSignature -->
<!-- Start DataObjectFormat -->
<!ELEMENT DataObjectFormat (Description?, ObjectIdentifier?, MimeType?, Encoding?)>
<!ATTLIST DataObjectFormat
ObjectReference CDATA #REQUIRED
>
<!ELEMENT MimeType (#PCDATA)>
<!ELEMENT Encoding (#PCDATA)>
<!-- End DataObjectFormat -->
<!-- Start CommitmentTypeIndication -->
<!ELEMENT CommitmentTypeIndication (CommitmentTypeId,
(ObjectReference* | AllSignedDataObjects), CommitmentTypeQualifiers?)
>
<!ELEMENT CommitmentTypeId (Identifier, Description?, DocumentationReferences?)>
<!ELEMENT ObjectReference (#PCDATA)>
<!ELEMENT AllSignedDataObjects ANY>
<!ELEMENT CommitmentTypeQualifiers (CommitmentTypeQualifier*)>
<!ELEMENT CommitmentTypeQualifier (#PCDATA%Any.ANY; )*>
<!-- End CommitmentTypeIndication -->
<!-- Start SignatureProductionPlace -->
<!ELEMENT SignatureProductionPlace (City?, StateOrProvince?, PostalCode?, CountryName?)>
<!ELEMENT City (#PCDATA)>
<!ELEMENT StateOrProvince (#PCDATA)>
<!ELEMENT PostalCode (#PCDATA)>
<!ELEMENT CountryName (#PCDATA)>
<!-- End SignatureProductionPlace -->
<!-- Start SignerRole -->
<!-- Start SignerRole -->
<!ELEMENT SignerRole (ClaimedRoles?, CertifiedRoles?)>
<!ELEMENT ClaimedRoles (ClaimedRole+)>
<!ELEMENT CertifiedRoles (CertifiedRole+)>
<!ELEMENT ClaimedRole (#PCDATA %Any.ANY; )*>
<!ELEMENT CertifiedRole (#PCDATA)>
<!ATTLIST CertifiedRole
Id ID #IMPLIED
>
<!-- End SignerRole -->
<!-- Start AllDataObjectsTimeStamp, IndividualDataObjectsTimeStamp, SignatureTimeStamp -->
<!ELEMENT AllDataObjectsTimeStamp (HashDataInfo+, (EncapsulatedTimeStamp | XMLTimeStamp))>
<!ELEMENT IndividualDataObjectsTimeStamp (HashDataInfo+, (EncapsulatedTimeStamp | XMLTimeStamp))>
<!ELEMENT SignatureTimeStamp (HashDataInfo+, (EncapsulatedTimeStamp | XMLTimeStamp))>
<!-- End AllDataObjectsTimeStamp, IndividualDataObjectsTimeStamp, SignatureTimeStamp -->
<!-- Start CompleteCertificateRefs -->
<!ELEMENT CompleteCertificateRefs (CertRefs)>
<!ATTLIST CompleteCertificateRefs
Id ID #IMPLIED
>
<!ELEMENT CertRefs (Cert+)>
<!-- End CompleteCertificateRefs -->
<!-- Start CompleteRevocationRefs -->
<!ELEMENT CompleteRevocationRefs (CRLRefs?, OCSPRefs?, OtherRefs?)>
<!ATTLIST CompleteRevocationRefs
Id ID #IMPLIED
>
<!ELEMENT CRLRefs (CRLRef+)>
<!ELEMENT OCSPRefs (OCSPRef+)>
<!ELEMENT OtherRefs (OtherRef+)>
<!ELEMENT CRLRef (DigestAlgAndValue,CRLIdentifier?)>
<!ELEMENT OCSPRef (OCSPIdentifier, DigestAlgAndValue?)>
<!ELEMENT OtherRef (#PCDATA %Any.ANY; )*>
<!ELEMENT DigestAlgAndValue (DigestMethod, DigestValue)>
<!ELEMENT CRLIdentifier (Issuer, IssueTime, Number?)>
<!ATTLIST Identifier
URI CDATA #IMPLIED
>
<!ELEMENT OCSPIdentifier (ResponderID, ProducedAt)>
<!ATTLIST Identifier
URI CDATA #IMPLIED
>
<!ELEMENT Issuer (#PCDATA)>
<!ELEMENT IssueTime (#PCDATA)>
<!ELEMENT Number (#PCDATA)>
<!ELEMENT ResponderID (#PCDATA)>
<!ELEMENT ProducedAt (#PCDATA)>
<!-- End CompleteRevocationRefs -->
<!-- Start SigAndRefsTimeStamp, RefsOnlyTimeStamp -->
<!ELEMENT SigAndRefsTimeStamp (HashDataInfo+, (EncapsulatedTimeStamp | XMLTimeStamp))>
<!ELEMENT RefsOnlyTimeStamp (HashDataInfo+, (EncapsulatedTimeStamp | XMLTimeStamp))>
<!-- End SigAndRefsTimeStamp, RefsOnlyTimeStamp -->
<!-- Start CertificateValues -->
<!ELEMENT CertificateValues (EncapsulatedX509Certificate | OtherCertificate)*>
<!ATTLIST CertificateValues
Id ID #IMPLIED
>
<!ELEMENT EncapsulatedX509Certificate (#PCDATA)>
<!ATTLIST EncapsulatedX509Certificate
Id ID #IMPLIED
>
<!ELEMENT OtherCertificate (#PCDATA %Any.ANY; )*>
<!-- End CertificateValues -->
<!-- Start RevocationValues -->
<!ELEMENT RevocationValues (CRLValues?, OCSPValues?, OtherValues?)>
<!ATTLIST RevocationValues
Id ID #IMPLIED
>
<!ELEMENT CRLValues (EncapsulatedCRLValue+)>
<!ELEMENT OCSPValues (EncapsulatedOCSPValue+)>
<!ELEMENT OtherValues (OtherValue+)>
<!ELEMENT EncapsulatedCRLValue (#PCDATA)>
<!ATTLIST EncapsulatedCRLValue
Id ID #IMPLIED
>
<!ELEMENT EncapsulatedOCSPValue (#PCDATA)>
<!ATTLIST EncapsulatedOCSPValue
Id ID #IMPLIED
>
<!ELEMENT OtherValue (#PCDATA%Any.ANY; )*>
<!-- End RevocationValues -->
<!-- Start ArchiveTimeStamp -->
<!ELEMENT ArchiveTimeStamp (HashDataInfo+, (EncapsulatedTimeStamp | XMLTimeStamp))>
<!-- End ArchiveTimeStamp -->
<?xml version="1.0" encoding="UTF-8"?>
<!ENTITY % Any.ANY ''>
<!ENTITY % XMLTimeStamp.ANY ''>
<!-- Start Any -->
<!ELEMENT Any (#PCDATA %Any.ANY;)*>
<!-- End Any -->
<!-- Start ObjectIdentifier -->
<!ELEMENT ObjectIdentifier (Identifier, Description?, DocumentationReferences?)>
<!ELEMENT Identifier (#PCDATA)>
<!ATTLIST Identifier
Qualifier (OIDAsURI | OIDAsURN) #IMPLIED
>
<!ELEMENT Description (#PCDATA)>
<!ELEMENT DocumentationReferences (DocumentationReference)+>
<!ELEMENT DocumentationReference (#PCDATA)>
<!-- End ObjectIdentifier -->
<!-- Start EncapsulatedPKIData -->
<!ELEMENT EncapsulatedPKIData (#PCDATA)>
<!ATTLIST EncapsulatedPKIData
Id ID #IMPLIED
>
<!-- End EncapsulatedPKIData -->
<!-- Start EncapsulatedTimeStamp -->
<!ELEMENT TimeStamp (HashDataInfo+, (EncapsulatedTimeStamp | XMLTimeStamp))>
<!ELEMENT HashDataInfo (Transforms?)>
<!ATTLIST HashDataInfo
uri CDATA #REQUIRED
>
<!ELEMENT EncapsulatedTimeStamp (#PCDATA)>
<!ATTLIST EncapsulatedTimeStamp
Id ID #IMPLIED
>
<!ELEMENT XMLTimeStamp (#PCDATA %XMLTimeStamp.ANY;)*>
<!-- End EncapsulatedTimeStamp -->
<!-- Start container types -->
<!-- Start QualifyingProperties -->
<!ELEMENT QualifyingProperties (SignedProperties, UnsignedProperties?)>
<!ATTLIST QualifyingProperties
Target CDATA #REQUIRED
Id ID #IMPLIED
>
<!ELEMENT SignedProperties (SignedSignatureProperties, SignedDataObjectProperties?)>
<!ATTLIST SignedProperties
Id ID #IMPLIED
>
<!ELEMENT UnsignedProperties (UnsignedSignatureProperties?, UnsignedDataObjectProperties?)>
<!ATTLIST UnsignedProperties
Id ID #IMPLIED
>
<!-- End QualifyingProperties -->
<!-- Start SignedSignatureProperties, SignedDataObjectProperties,
UnsignedSignatureProperties, UnsignedDataObjectProperties -->
<!ELEMENT SignedSignatureProperties (SigningTime, SigningCertificate,
SignaturePolicyIdentifier, SignatureProductionPlace?, SignerRole?)
>
<!ELEMENT SignedDataObjectProperties (DataObjectFormat*,
CommitmentTypeIndication*, AllDataObjectsTimeStamp*, IndividualDataObjectsTimeStamp*)
>
<!ELEMENT UnsignedSignatureProperties (CounterSignature*, SignatureTimeStamp*,
CompleteCertificateRefs?, CompleteRevocationRefs?,
(SigAndRefsTimeStamp* | RefsOnlyTimeStamp*), CertificateValues?,
RevocationValues?, ArchiveTimeStamp*)
>
<!ELEMENT UnsignedDataObjectProperties (UnsignedDataObjectProperty*)>
<!ELEMENT UnsignedDataObjectProperty (#PCDATA %Any.ANY; )*>
<!-- End SignedSignatureProperties, SignedDataObjectProperties,
UnsignedSignatureProperties, UnsignedDataObjectProperties -->
<!-- Start QualifyingPropertiesReference -->
<!ELEMENT QualifyingPropertiesReference (Transforms?)>
<!ATTLIST QualifyingPropertiesReference
URI CDATA #REQUIRED
Id ID #IMPLIED
>
<!-- End QualifyingPropertiesReference -->
<!-- End container types -->
<!-- Start SigningTime -->
<!ELEMENT SigningTime (#PCDATA)>
<!-- End SigningTime -->
<!-- Start SigningCertificate -->
<!ELEMENT SigningCertificate (Cert+)>
<!ELEMENT Cert (CertDigest, IssuerSerial)>
<!ELEMENT CertDigest (DigestMethod, DigestValue)>
<!ELEMENT IssuerSerial (X509IssuerName, X509SerialNumber)>
<!-- End SigningCertificate -->
<!-- Start SignaturePolicyIdentifier -->
<!ELEMENT SignaturePolicyIdentifier (SignaturePolicyId | SignaturePolicyImplied)>
<!ELEMENT SignaturePolicyId (SigPolicyId, Transforms?, SigPolicyHash, SigPolicyQualifiers?)>
<!ELEMENT SignaturePolicyImplied ANY>
<!ELEMENT SigPolicyId (Identifier, Description?, DocumentationReferences?)>
<!ELEMENT SigPolicyHash (DigestMethod, DigestValue)>
<!ELEMENT SigPolicyQualifiers (SigPolicyQualifier+)>
<!ELEMENT SigPolicyQualifier (#PCDATA %Any.ANY; )*>
<!-- End SignaturePolicyIdentifier -->
<!-- Start SPURI and SPUserNotice -->
<!ELEMENT SPURI (#PCDATA)>
<!ELEMENT SPUserNotice (NoticeRef?, ExplicitText?)>
<!ELEMENT NoticeRef (Organization, NoticeNumbers)>
<!ELEMENT ExplicitText (#PCDATA)>
<!ELEMENT Organization (#PCDATA)>
<!ELEMENT NoticeNumbers (#PCDATA)*>
<!-- End SPURI and SPUserNotice -->
<!-- Start CounterSignature -->
<!ELEMENT CounterSignature (Signature)>
<!-- End CounterSignature -->
<!-- Start DataObjectFormat -->
<!ELEMENT DataObjectFormat (Description?, ObjectIdentifier?, MimeType?, Encoding?)>
<!ATTLIST DataObjectFormat
ObjectReference CDATA #REQUIRED
>
<!ELEMENT MimeType (#PCDATA)>
<!ELEMENT Encoding (#PCDATA)>
<!-- End DataObjectFormat -->
<!-- Start CommitmentTypeIndication -->
<!ELEMENT CommitmentTypeIndication (CommitmentTypeId,
(ObjectReference* | AllSignedDataObjects), CommitmentTypeQualifiers?)
>
<!ELEMENT CommitmentTypeId (Identifier, Description?, DocumentationReferences?)>
<!ELEMENT ObjectReference (#PCDATA)>
<!ELEMENT AllSignedDataObjects ANY>
<!ELEMENT CommitmentTypeQualifiers (CommitmentTypeQualifier*)>
<!ELEMENT CommitmentTypeQualifier (#PCDATA%Any.ANY; )*>
<!-- End CommitmentTypeIndication -->
<!-- Start SignatureProductionPlace -->
<!ELEMENT SignatureProductionPlace (City?, StateOrProvince?, PostalCode?, CountryName?)>
<!ELEMENT City (#PCDATA)>
<!ELEMENT StateOrProvince (#PCDATA)>
<!ELEMENT PostalCode (#PCDATA)>
<!ELEMENT CountryName (#PCDATA)>
<!-- End SignatureProductionPlace -->
<!-- Start SignerRole -->
<!-- Start SignerRole -->
<!ELEMENT SignerRole (ClaimedRoles?, CertifiedRoles?)>
<!ELEMENT ClaimedRoles (ClaimedRole+)>
<!ELEMENT CertifiedRoles (CertifiedRole+)>
<!ELEMENT ClaimedRole (#PCDATA %Any.ANY; )*>
<!ELEMENT CertifiedRole (#PCDATA)>
<!ATTLIST CertifiedRole
Id ID #IMPLIED
>
<!-- End SignerRole -->
<!-- Start AllDataObjectsTimeStamp, IndividualDataObjectsTimeStamp, SignatureTimeStamp -->
<!ELEMENT AllDataObjectsTimeStamp (HashDataInfo+, (EncapsulatedTimeStamp | XMLTimeStamp))>
<!ELEMENT IndividualDataObjectsTimeStamp (HashDataInfo+, (EncapsulatedTimeStamp | XMLTimeStamp))>
<!ELEMENT SignatureTimeStamp (HashDataInfo+, (EncapsulatedTimeStamp | XMLTimeStamp))>
<!-- End AllDataObjectsTimeStamp, IndividualDataObjectsTimeStamp, SignatureTimeStamp -->
<!-- Start CompleteCertificateRefs -->
<!ELEMENT CompleteCertificateRefs (CertRefs)>
<!ATTLIST CompleteCertificateRefs
Id ID #IMPLIED
>
<!ELEMENT CertRefs (Cert+)>
<!-- End CompleteCertificateRefs -->
<!-- Start CompleteRevocationRefs -->
<!ELEMENT CompleteRevocationRefs (CRLRefs?, OCSPRefs?, OtherRefs?)>
<!ATTLIST CompleteRevocationRefs
Id ID #IMPLIED
>
<!ELEMENT CRLRefs (CRLRef+)>
<!ELEMENT OCSPRefs (OCSPRef+)>
<!ELEMENT OtherRefs (OtherRef+)>
<!ELEMENT CRLRef (DigestAlgAndValue,CRLIdentifier?)>
<!ELEMENT OCSPRef (OCSPIdentifier, DigestAlgAndValue?)>
<!ELEMENT OtherRef (#PCDATA %Any.ANY; )*>
<!ELEMENT DigestAlgAndValue (DigestMethod, DigestValue)>
<!ELEMENT CRLIdentifier (Issuer, IssueTime, Number?)>
<!ATTLIST Identifier
URI CDATA #IMPLIED
>
<!ELEMENT OCSPIdentifier (ResponderID, ProducedAt)>
<!ATTLIST Identifier
URI CDATA #IMPLIED
>
<!ELEMENT Issuer (#PCDATA)>
<!ELEMENT IssueTime (#PCDATA)>
<!ELEMENT Number (#PCDATA)>
<!ELEMENT ResponderID (#PCDATA)>
<!ELEMENT ProducedAt (#PCDATA)>
<!-- End CompleteRevocationRefs -->
<!-- Start SigAndRefsTimeStamp, RefsOnlyTimeStamp -->
<!ELEMENT SigAndRefsTimeStamp (HashDataInfo+, (EncapsulatedTimeStamp | XMLTimeStamp))>
<!ELEMENT RefsOnlyTimeStamp (HashDataInfo+, (EncapsulatedTimeStamp | XMLTimeStamp))>
<!-- End SigAndRefsTimeStamp, RefsOnlyTimeStamp -->
<!-- Start CertificateValues -->
<!ELEMENT CertificateValues (EncapsulatedX509Certificate | OtherCertificate)*>
<!ATTLIST CertificateValues
Id ID #IMPLIED
>
<!ELEMENT EncapsulatedX509Certificate (#PCDATA)>
<!ATTLIST EncapsulatedX509Certificate
Id ID #IMPLIED
>
<!ELEMENT OtherCertificate (#PCDATA %Any.ANY; )*>
<!-- End CertificateValues -->
<!-- Start RevocationValues -->
<!ELEMENT RevocationValues (CRLValues?, OCSPValues?, OtherValues?)>
<!ATTLIST RevocationValues
Id ID #IMPLIED
>
<!ELEMENT CRLValues (EncapsulatedCRLValue+)>
<!ELEMENT OCSPValues (EncapsulatedOCSPValue+)>
<!ELEMENT OtherValues (OtherValue+)>
<!ELEMENT EncapsulatedCRLValue (#PCDATA)>
<!ATTLIST EncapsulatedCRLValue
Id ID #IMPLIED
>
<!ELEMENT EncapsulatedOCSPValue (#PCDATA)>
<!ATTLIST EncapsulatedOCSPValue
Id ID #IMPLIED
>
<!ELEMENT OtherValue (#PCDATA%Any.ANY; )*>
<!-- End RevocationValues -->
<!-- Start ArchiveTimeStamp -->
<!ELEMENT ArchiveTimeStamp (HashDataInfo+, (EncapsulatedTimeStamp | XMLTimeStamp))>
<!-- End ArchiveTimeStamp -->
|