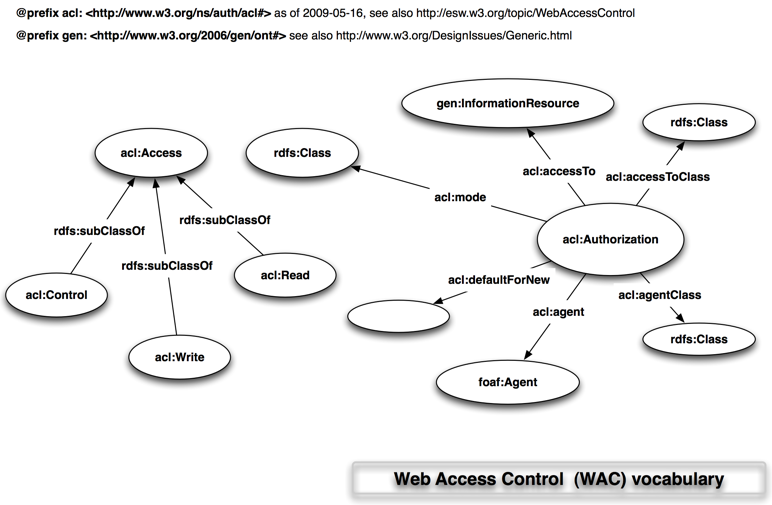
WebAccessControl/Vocabulary
Appearance
Discussion of the WAC vocabulary
Questions regarding the current vocabulary:
- should range of
acl:modebeacl:Accessrather thanrdfs:Class? - what is the range of
acl:defaultForNew? - should range of acl:accessToClass be something more specific than
rdfs:Class, such as http://purl.org/dc/dcmitype/Dataset orvoid:Datasetor some POWDER stuff? - shouldn't there be a property between
acl:Controlandgen:[[InformationResource]]such asacl:controls?
Open issues/feature requests:
- what about roles? do we need them/need to express them?
- what about ownership? shall we flag who owns a resource or is this implicitly assumed by
acl:Control? - what about dynamics? imagine a situation where you are allowed access for, say, a day. shall we explicitly state the time frame for which
acl:the Authorisationis valid? - there is an implicit assumption that the
foaf:members of a resource which is the object of anacl:agentClasshave the same WebID as used in FOAF+SSL; this is not necessary the case, take for example the case where I'd like to gain access to a resource using my WebID http://sw-app.org/mic.xhtml#i and someone stated that all the members of DERI have access to it in her ACL. In the DERI group there will be a statement:DERI foaf:member <http://www.deri.ie/about/team/member/Michael_Hausenblas#me>and unless it is known that these two WebIDs refer to the same person, the system will not grant me access.
Related Work
- Fausto Giunchiglia, R Zhang and B.Crispo, University of Trento, " Ontology Driven Access Control", DISI Technical Report. Uses DL, and (sub)properties (rather than (sub)classes as in WACL) for permissions. ( But see also an initial critique of that paper on the swig irc channel )