Visual marks play critical roles in the physical world, but their use in the cyber
world is limited because there they are easy to forge, tamper with and copy onto
unauthorized contents. This note therefore describes a new type of visual marks that are
secure because digital signatures are embedded in them and that can be used with a wide
variety of cyber-world systems. It also shows their application to seal systems for WWW
site authentication.
This document is a submission to the World Wide Web Consortium from
Hitachi Ltd. (see Submission Request, W3C Staff Comment). For a full list of all acknowledged Submissions, please see Acknowledged Submissions to W3C.
This document is a NOTE made available by W3C for discussion only. This indicates no
endorsement of its content, nor that W3C has had any editorial control in its preparation,
nor that W3C has, is, or will be allocating any resources to the issues addressed by the
NOTE.
A list of current W3C technical documents can be found at the Technical Reports page.
Table of Contents
The number of Internet users is continuously increasing, and network-based social
activities such as EC (electronic commerce) are becoming popular in many fields. On the
other hand, however, social problems related to the networks are also increasing. It is
therefore necessary to clarify the requirements that must be met by networks that serve as
social infrastructures and to establish techniques for meeting these requirements. One of
the most important requirements is that the networks be trustworthy, and various
authentication techniques for meeting this requirement by using digital signatures have
been developed. They are, however, not sufficiently clear. That is, they are not easily
understood by nonprofessional people. In SSL (Secure Sockets Layer) and S-HTTP (Secure
Hyper Text Transfer Protocol), for example, users can not easily understand what
authentication means. Networks that are trusted therefore are networks providing not only
security but also clarity.
Visual marks, such as traffic signals, play critical roles in the physical world. They
are familiar to nonprofessional people and can convey information clearly. Thus one
promising approach to meeting the clarity requirement is to incorporate visual marks into
the cyber world. Such marks are already used in the following ways:
- (1) Content Guarantee
- Marks are pasted on Web pages and show the results of evaluation or rating (e.g., marks
indicating the top 1% sites, and marks showing that sites are recommended by the Education
Ministry).
- (2) Service Availability Indication
- Marks such as credit card marks show services available on the Web sites.
- (3) Membership Indication
- Marks such as insignia show that the Web sites belong to specific groups.
- (4) Ownership Indication
- Brand marks or logos indicate the ownership of the Web sites.
- (5) Used as Money
- Some marks are used as substitutes for money (e.g., the coupons of fast food shops).
Thus visual marks are widely used in cyber world. These marks have serious problems,
however, due to the properties of cyber worlds. Specifically, they are easy to forge,
tamper with, and copy onto other Web sites. In summary, conventional visual marks are
clear but are insufficiently secure.
A Visual Mark for the Cyber World(VM) is a new type of visual mark suitable for use in
the cyber world. It is intended to make networks trustworthy by making visual marks
secure.
VMs are made of drawings and are image data, such as bitmap graphics or JPEG files.
They are placed on data that represent objects in the cyber world, and they carry
information about that data.
FIGUREs are drawings from which VMs are made, and DATA is
data on which VMs are pasted.
Figure 1 shows examples of FIGUREs. And as shown in Fig. 2, a VM is a simply FIGURE
into which a digital signature has been embedded by digital watermarking [1]. This
signature is a signature for both the FIGURE and the DATA on which the VM is pasted.
Additional application-specific information may also be embedded into the FIGURE.
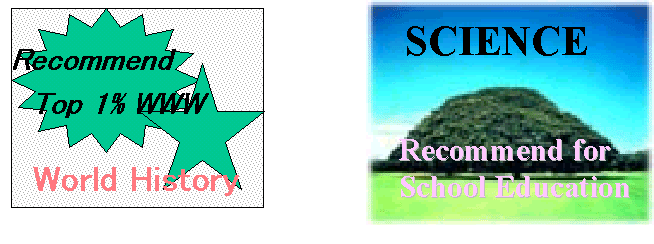
Fig. 1. Examples of FIGUREs.
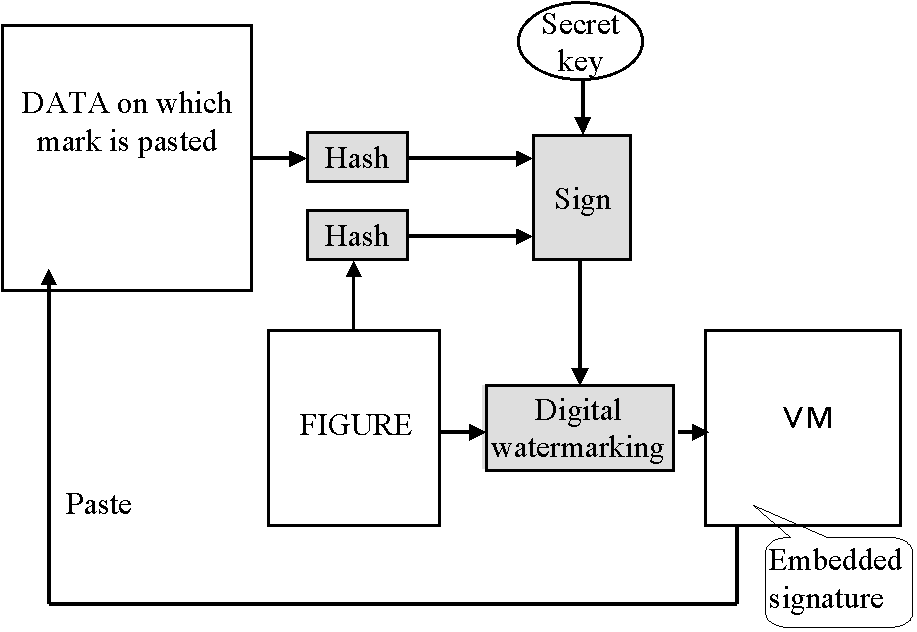
Fig. 2. VMs issuing system.
White and gray area respectively represent data and processes.
A VM is issued (Fig. 2) by having the issuer sign for the DATA and the FIGURE and then
embedding the signature in the FIGURE. And as shown in Fig. 3, a VM is verified by first
cutting it out of the DATA and then extracting and verifying the signature. If the
verification is successful the system guarantees the following:
- The VM is not forged and has not been tampered with.
- The VM is on authorized data.
- The DATA has not been tampered with.
- The VM was generated and placed on the DATA by the person indicated by the verification
key (public key).
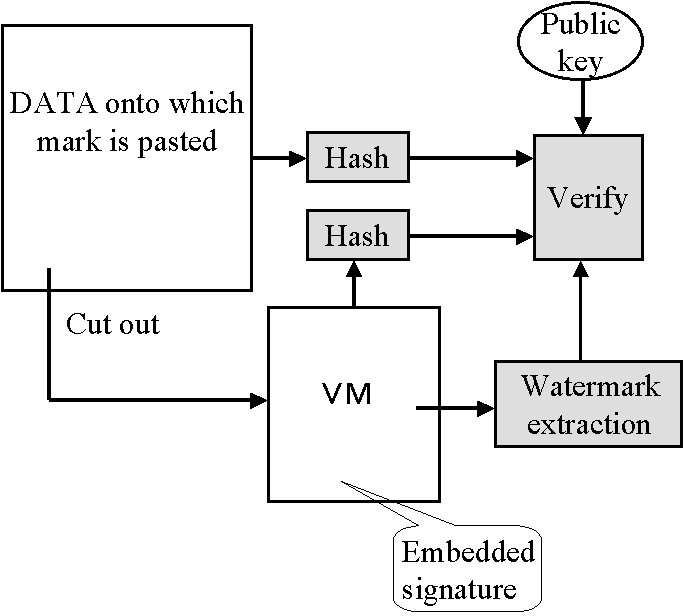
Fig. 3. VMs verifying system.
(1) Clarity
VMs are easily understood because the watermarking does not degrade the clarity of the
FIGUREs from which they are made.
(2) Security
It is obvious from Figs. 2 and 3 that the security of VMs is equivalent to that of their
signatures.
(3) Portability
Equivalent clarity and security could be provided by using a simple combination of visual
marks and digital signatures, but VMs are more portable than the simple combination
because the clarity measures (visual figures) and the security measures (digital
signatures) are consolidated in a single object.
This chapter illustrates a VM application to a WWW authentication scenario in which
there are four players:
WWW site owner (Owner).
WWW site user who accesses the Owner's WWW site (User).
Person who issues a guarantee mark for the Owner's WWW site (Guarantor).
Certificate Authority who authenticates the Owner's public key (CA).
When the owner asks the guarantor to issue a guarantee mark for the owner's WWW site,
the guarantor issues it and sends it to the owner, who places it on the pages of the WWW
site. The guarantee mark may be a rating of the site, a certification of its suitability
for use in schools, or any other information relevant to the site. A user accessing the
site can get information about it simply by looking at the guarantee mark and can verify
the guarantee mark when necessary (e.g., when sending a credit card number to the site).
We use VMs for guarantee marks, and Fig. 4 shows that the system for issuing these
guarantee VMs is simply the basic VM issuing system extended to include a signature for
the IP address (URL) of the WWW site to be guaranteed. This signature is needed to prevent
WWW site disguise: the copying of both the WWW page data and its guarantee mark to the WWW
site of an attacker who pretends to be the legal owner of its content.
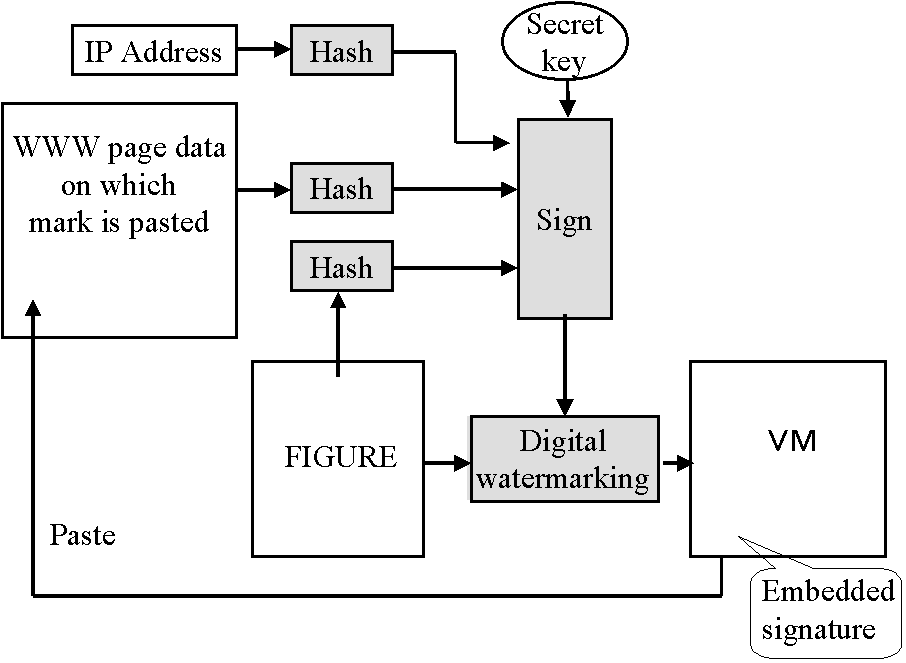
Fig. 4. System issuing an VMs for WWW authentication.
This protocol description uses the following terminology.
SKx: secret key of player x.
PKx: public key of player x.
Enc(DATA, K): result of encrypting DATA with key K.
IP-ADDRESS: IP address (URL) of the WWW site to be marked.
W-DATA: DATA defining pages of the WWW site. This may be XML source code.
X | Y: concatenation of data X and data Y.
The protocols for issuing and authenticating VMs are illustrated in Fig. 5, and there
are four steps in the protocol for issuing them.
- Step 1: The owner applies for an VM by sending to the guarantor the
IP-ADDRESS, the W-DATA, and a Memo specifying the kind of VM the owner wants.
- Step 2: The guarantor issues a VM by the following substeps:
-
- (2-1) Select a FIGURE appropriate to the Memo and then generate a
signature for the FIGURE, IP-ADDRESS, and W-DATA. This signature is
ENC( Hash(FIGURE) | Hash(IP-ADDRESS) | Hash(W-DATA),
SKGuarantor).
- (2-2) Generate a VM by embedding the signature in the FIGURE.
- Step 3: The guarantor sends the VM to the owner.
- Step 4: The owner pastes the VM on the WWW page.
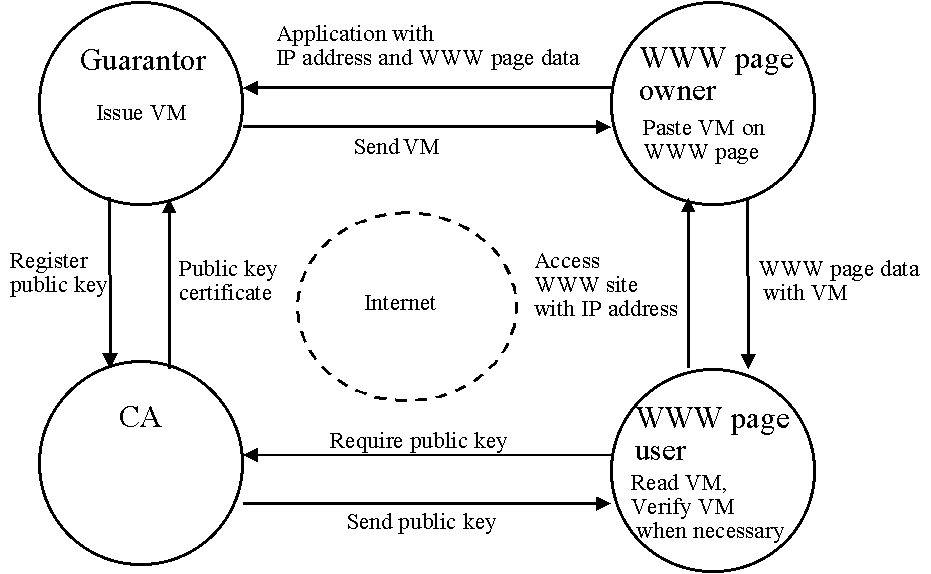
Fig. 5. Protocols for VMs application.
The protocol for authenticating VMs has three steps.
- Step 1: A user accesses the owner's WWW site by using an IP address.
- Step 2: The owner sends the user WWW data (i.e., XML source codes)
accompanied by a VM.
- Step 3: The user gets information by looking at the VM and, when
necessary, verifies the VM by the following substeps:
-
- (3-1) Cut the VM from the WWW data, and extract the signature from the
VM.
- (3-2) Verify the signature by using PKGuarantor,. In the
verification, hash values are calculated for the XML source codes and IP address of the
accessed site and for the FIGURE that was used to make the VM.
- (3-3) If the verification is successful, the protocol guarantees the
following:
-
- The accessed WWW site is the one for which the guarantor issued an
VM.
- The VM is on the intended W-DATA.
- Neither the VM nor the W-DATA have been tampered with.
These application protocols have been implemented in C language, and Fig. 6 shows VMs
made from the FIGUREs in Fig. 1. A roughly 2-K Bytes digital signature is embedded in each
VM.

Fig. 6. VMs generated from the FIGUREs in Fig. 1.
(1) Clarity
As can be seen by comparing Figures 1 and 6, the clarity of the FIGUREs is not degraded by
watermarking.
(2) Security
Three types of attack are possible.
- Type 1: Attack VMs themselves ( i.e., forge, or tampering with VMs).
- Type 2: Copy VMs onto unauthorized Web pages.
- Type 3: Copy both WWW page data and its VM to the WWW site of someone who pretends to be
the legal owner of the WWW data.
As mentioned in Section2, the security against the first and second types of attacks is
equivalent to the security of the embedded signature. The security against third type is
also the same as that of the signature because VMs contain the signature for the IP
address of the correct WWW site.
(3) Portability
This issue will be discussed in next chapter by comparing VMs with alternative approaches.
This chapter compares VMs with the following three alternative approaches to WWW
authentication.
- Simple Marks:
- The guarantor issues a mark that the owner attaches to the WWW page.
- Simple Signatures:
- The guarantor issues a signature for the WWW page, and the owner
attaches it to the page.
- Simple Combination of Marks and Signatures:
- The guarantor issues a mark and signature
for both the WWW page and the mark. The owner attaches the mark and signature to the page.
It is clear from the comparison results summarize in Table 1 that simple marks are
clear and portable but of course not secure. And because a digital signature expresses
nothing by itself, it tells a WWW user nothing about the WWW page unless the user goes
through the verification process. Simple signatures, although secure and reasonably
portable, thus do not meet a user's needs because their meaning is not clear.
Table 1. Comparison of Alternative Approaches.
| No. |
Methods |
Security |
Clarity |
Portabiligy |
| 1 |
Simple Marks |
No Good |
Good |
Good |
| 2 |
Simple Signature |
Good |
No Good |
Not so Bad |
| 3 |
Simple combination of marks and Signature |
Good |
Good |
No Good |
| 4 |
VMs |
Good |
Good |
Not so Bad |
A WWW owner using a combination of marks and signatures needs to attach a mark and the
corresponding signature to the WWW page in such a way that there is a link between them
(e.g., clicking the mark causes the signature to be verified). This attachment needs to be
standardized so that WWW users can use a common program to verify signatures. Such
standardization requires extensive and continuous effort because the languages for
describing WWW pages are continuously evolving along with the WWW managing systems. VMs
also require standardization, but this standardization should be much easier because all
that needs to be standardized is the way of attaching VMs. That is, there is no need for
standardization of the way of linking marks and signatures.
This paper described VMs; trusted visual marks for the authentication of Web sites. The
paper has shown that VMs are as easily understood as visual marks, as secure as digital
signatures, and are more portable than a simple combination of visual marks and digital
signatures. VMs can be used with other Web related authentication systems such as
Signed-XML and can then improve their clarity.





