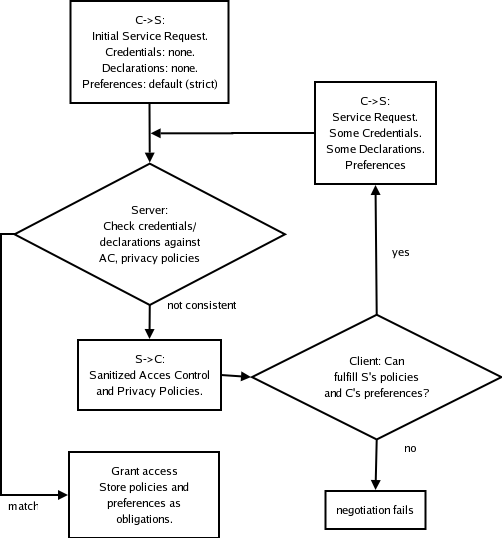
What happens? High-level view.
-
Client attempts to access a service, provides data handling
preferences and some credentials / declarations.
- Initial contact: no credentials / declarations.
- Default preferences at initial contact: maximum privacy.
-
Server decision point: If access control policy matches, then
grant access, and fulfill obligations.
-
Server presents its policies to client.
-
Client decision point: If access control policy can be
matched, then assemble credentials / declarations and go to
step 1. Else fail.

