HTML5
A vocabulary and associated APIs for HTML and XHTML
This is revision 1.5612.
This is revision 1.5612.
Navigator objectThe navigator
attribute of the Window interface must return an
instance of the Navigator interface, which represents
the identity and state of the user agent (the client), and allows
Web pages to register themselves as potential protocol and content
handlers:
interface Navigator {
// objects implementing this interface also implement the interfaces given below
};
Navigator implements NavigatorID;
Navigator implements NavigatorOnLine;
Navigator implements NavigatorContentUtils;
Navigator implements NavigatorStorageUtils;
These interfaces are defined separately so that other
specifications can re-use parts of the Navigator
interface.
[NoInterfaceObject]
interface NavigatorID {
readonly attribute DOMString appName;
readonly attribute DOMString appVersion;
readonly attribute DOMString platform;
readonly attribute DOMString userAgent;
};
In certain cases, despite the best efforts of the entire industry, Web browsers have bugs and limitations that Web authors are forced to work around.
This section defines a collection of attributes that can be used to determine, from script, the kind of user agent in use, in order to work around these issues.
Client detection should always be limited to detecting known current versions; future versions and unknown versions should always be assumed to be fully compliant.
navigator . appNameReturns the name of the browser.
navigator . appVersionReturns the version of the browser.
navigator . platformReturns the name of the platform.
navigator . userAgentReturns the complete User-Agent header.
appNameMust return either the string "Netscape" or the full name of the browser, e.g. "Mellblom Browsernator".
appVersionMust return either the string "4.0" or a string representing the version of the browser in detail, e.g. "1.0 (VMS; en-US) Mellblomenator/9000".
platformMust return either the empty string or a string representing the platform on which the browser is executing, e.g. "MacIntel", "Win32", "FreeBSD i386", "WebTV OS".
userAgentMust return the string used for the value of the "User-Agent" header in HTTP requests, or the empty string if no such header is ever sent.
Any information in this API that varies from user to user can be used to profile the user. In fact, if enough such information is available, a user can actually be uniquely identified. For this reason, user agent implementors are strongly urged to include as little information in this API as possible.
[NoInterfaceObject]
interface NavigatorContentUtils {
// content handler registration
void registerProtocolHandler(DOMString scheme, DOMString url, DOMString title);
void registerContentHandler(DOMString mimeType, DOMString url, DOMString title);
DOMString isProtocolHandlerRegistered(DOMString scheme, DOMString url);
DOMString isContentHandlerRegistered(DOMString mimeType, DOMString url);
void unregisterProtocolHandler(DOMString scheme, DOMString url);
void unregisterContentHandler(DOMString mimeType, DOMString url);
};
The registerProtocolHandler()
method allows Web sites to register themselves as possible handlers
for particular schemes. For example, an online telephone messaging
service could register itself as a handler of the sms:
scheme, so that if the user clicks on such a link, he is given the
opportunity to use that Web site. Analogously, the registerContentHandler()
method allows Web sites to register themselves as possible handlers
for content in a particular MIME type. For example, the
same online telephone messaging service could register itself as a
handler for text/vcard files, so that if the user has
no native application capable of handling vCards, his Web browser
can instead suggest he use that site to view contact information
stored on vCards that he opens. [RFC5724]
RFC6350
navigator . registerProtocolHandler(scheme, url, title)navigator . registerContentHandler(mimeType, url, title)Registers a handler for the given scheme or content type, at the given URL, with the given title.
The string "%s" in the URL is used as a
placeholder for where to put the URL of the content to be
handled.
Throws a SecurityError exception if the user agent
blocks the registration (this might happen if trying to register
as a handler for "http", for instance).
Throws a SyntaxError if the "%s" string is missing in the URL.
User agents may, within the constraints described in this section, do whatever they like when the methods are called. A UA could, for instance, prompt the user and offer the user the opportunity to add the site to a shortlist of handlers, or make the handlers his default, or cancel the request. UAs could provide such a UI through modal UI or through a non-modal transient notification interface. UAs could also simply silently collect the information, providing it only when relevant to the user.
User agents should keep track of which sites have registered handlers (even if the user has declined such registrations) so that the user is not repeatedly prompted with the same request.
The arguments to the methods have the following meanings and corresponding implementation requirements. The requirements that involve throwing exceptions must be processed in the order given below, stopping at the first exception thrown. (So the exceptions for the first argument take precedence over the exceptions for the second argument.)
registerProtocolHandler() only)A scheme, such as mailto or web+auth.
The scheme must be compared in an ASCII
case-insensitive manner by user agents for the purposes of
comparing with the scheme part of URLs that they consider against
the list of registered handlers.
The scheme value, if it contains a colon
(as in "mailto:"), will never match anything, since
schemes don't contain colons.
If the registerProtocolHandler()
method is invoked with a scheme that is neither a
whitelisted scheme nor a scheme whose value starts
with the substring "web+" and otherwise
contains only characters in the range lowercase ASCII letters, the user agent must throw a
SecurityError exception.
The following schemes are the whitelisted schemes:
ircmailtommsnewsnntpsmssmstotelurnwebcalxmppThis list can be changed. If there are schemes that should be added, please send feedback.
registerContentHandler() only)A MIME type, such as
model/vnd.flatland.3dml or
application/vnd.google-earth.kml+xml. The MIME
type must be compared in an ASCII
case-insensitive manner by user agents for the purposes of
comparing with MIME types of documents that they consider against
the list of registered handlers.
User agents must compare the given values only to the MIME type/subtype parts of content types, not to the complete type including parameters. Thus, if mimeType values passed to this method include characters such as commas or whitespace, or include MIME parameters, then the handler being registered will never be used.
The type is compared to the MIME type used by the user agent after the sniffing algorithms have been applied.
If the registerContentHandler()
method is invoked with a MIME type that is in the
type blacklist or that the user agent has deemed a
privileged type, the user agent must throw a
SecurityError exception.
The following MIME types are in the type blacklist:
application/x-www-form-urlencodedapplication/xhtml+xmlapplication/xmlimage/gifimage/jpegimage/pngimage/svg+xmlmultipart/x-mixed-replacetext/cache-manifesttext/csstext/htmltext/pingtext/plaintext/xmlapplication/rss+xml and application/atom+xmlThis list can be changed. If there are schemes that should be added, please send feedback.
A string used to build the URL of the page that will handle the requests.
User agents must throw a SyntaxError exception if
the url argument passed to one of these
methods does not contain the exact literal string
"%s".
User agents must throw a SyntaxError if resolving the url
argument relative to the entry script's base URL, is not successful.
The resulting absolute URL would by
definition not be a valid URL as it would include the
string "%s" which is not a valid component
in a URL.
User agents must throw a SecurityError exception if
the resulting absolute URL has an origin
that differs from the origin of the entry
script.
This is forcibly the case if the %s placeholder is in the scheme, host, or port
parts of the URL.
The resulting absolute URL is the proto-URL. It identifies the handler for the purposes of the methods described below.
When the user agent uses this handler, it must replace the
first occurrence of the exact literal string "%s" in the url argument with
an escaped version of the absolute URL of the content
in question (as defined below), then resolve the resulting URL, relative to the base URL of the entry
script at the time the registerContentHandler()
or registerProtocolHandler()
methods were invoked, and then navigate an appropriate browsing context to the
resulting URL using the GET method (or equivalent for
non-HTTP URLs).
To get the escaped version of the absolute URL of the content in question, the user agent must replace every character in that absolute URL that doesn't match the <query> production defined in RFC 3986 by the percent-encoded form of that character. [RFC3986]
If the user had visited a site at http://example.com/ that made the following
call:
navigator.registerContentHandler('application/x-soup', 'soup?url=%s', 'SoupWeb™')
...and then, much later, while visiting http://www.example.net/, clicked on a link such
as:
<a href="chickenkïwi.soup">Download our Chicken Kïwi soup!</a>
...then, assuming this chickenkïwi.soup file
was served with the MIME type
application/x-soup, the UA might navigate to the
following URL:
http://example.com/soup?url=http://www.example.net/chickenk%C3%AFwi.soup
This site could then fetch the chickenkïwi.soup
file and do whatever it is that it does with soup (synthesize it
and ship it to the user, or whatever).
A descriptive title of the handler, which the UA might use to remind the user what the site in question is.
This section does not define how the pages registered by these methods are used, beyond the requirements on how to process the url value (see above). To some extent, the processing model for navigating across documents defines some cases where these methods are relevant, but in general UAs may use this information wherever they would otherwise consider handing content to native plugins or helper applications.
UAs must not use registered content handlers to handle content that was returned as part of a non-GET transaction (or rather, as part of any non-idempotent transaction), as the remote site would not be able to fetch the same data.
In addition to the registration methods, there are also methods for determining if particular handlers have been registered, and for unregistering handlers.
navigator . isProtocolHandlerRegistered(scheme, url)navigator . isContentHandlerRegistered(mimeType, url)Returns one of the following strings describing the state of the handler given by the arguments:
new
registered
declined
navigator . unregisterProtocolHandler(scheme, url)navigator . unregisterContentHandler(mimeType, url)Unregisters the handler given by the arguments.
The isProtocolHandlerRegistered()
method must return the handler state string that most
closely describes the current state of the handler described by the
two arguments to the method, where the first argument gives the
scheme and the second gives the string used to build the
URL of the page that will handle the requests.
The first argument must be compared to the schemes for which custom protocol handlers are registered in an ASCII case-insensitive manner to find the relevant handlers.
The second argument must be preprocessed as described below, and if that is successful, must then be matched against the proto-URLs of the relevant handlers to find the described handler.
The isContentHandlerRegistered()
method must return the handler state string that most
closely describes the current state of the handler described by the
two arguments to the method, where the first argument gives the
MIME type and the second gives the string used to build
the URL of the page that will handle the requests.
The first argument must be compared to the MIME types for which custom content handlers are registered in an ASCII case-insensitive manner to find the relevant handlers.
The second argument must be preprocessed as described below, and if that is successful, must then be matched against the proto-URLs of the relevant handlers to find the described handler.
The handler state strings are the following strings. Each string describes several situations, as given by the following list.
new
registered
declined
The unregisterProtocolHandler()
method must unregister the handler described by the two arguments to
the method, where the first argument gives the scheme and the second
gives the string used to build the URL of the page that
will handle the requests.
The first argument must be compared to the schemes for which custom protocol handlers are registered in an ASCII case-insensitive manner to find the relevant handlers.
The second argument must be preprocessed as described below, and if that is successful, must then be matched against the proto-URLs of the relevant handlers to find the described handler.
The unregisterContentHandler()
method must unregister the handler described by the two arguments to
the method, where the first argument gives the MIME
type and the second gives the string used to build the
URL of the page that will handle the requests.
The first argument must be compared to the MIME types for which custom content handlers are registered in an ASCII case-insensitive manner to find the relevant handlers.
The second argument must be preprocessed as described below, and if that is successful, must then be matched against the proto-URLs of the relevant handlers to find the described handler.
The second argument of the four methods described above must be preprocessed as follows:
If the string does not contain the substring "%s", abort these steps. There's no matching
handler.
Resolve the string relative to the base URL of the entry script.
If this fails, then throw a SyntaxError
exception, aborting the method.
If the resoluting absolute URL's origin is not the same origin as that of the entry script throw a SecurityError exception, aborting the method.
Return the resulting absolute URL as the result of preprocessing the argument.
These mechanisms can introduce a number of concerns, in particular privacy concerns.
Hijacking all Web usage. User agents should not
allow schemes that are key to its normal operation, such as
http or https, to be rerouted through
third-party sites. This would allow a user's activities to be
trivially tracked, and would allow user information, even in secure
connections, to be collected.
Hijacking defaults. It is strongly recommended that user agents do not automatically change any defaults, as this could lead the user to send data to remote hosts that the user is not expecting. New handlers registering themselves should never automatically cause those sites to be used.
Registration spamming. User agents should
consider the possibility that a site will attempt to register a
large number of handlers, possibly from multiple domains (e.g. by
redirecting through a series of pages each on a different domain,
and each registering a handler for video/mpeg —
analogous practices abusing other Web browser features have been
used by pornography Web sites for many years). User agents should
gracefully handle such hostile attempts, protecting the user.
Misleading titles. User agents should not rely
wholly on the title argument to the methods when
presenting the registered handlers to the user, since sites could
easily lie. For example, a site hostile.example.net
could claim that it was registering the "Cuddly Bear Happy Content
Handler". User agents should therefore use the handler's domain in
any UI along with any title.
Hostile handler metadata. User agents should protect against typical attacks against strings embedded in their interface, for example ensuring that markup or escape characters in such strings are not executed, that null bytes are properly handled, that over-long strings do not cause crashes or buffer overruns, and so forth.
Leaking Intranet URLs. The mechanism described in this section can result in secret Intranet URLs being leaked, in the following manner:
No actual confidential file data is leaked in this manner, but
the URLs themselves could contain confidential information. For
example, the URL could be
http://www.corp.example.com/upcoming-aquisitions/the-sample-company.egf,
which might tell the third party that Example Corporation is
intending to merge with The Sample Company. Implementors might wish
to consider allowing administrators to disable this feature for
certain subdomains, content types, or schemes.
Leaking secure URLs. User agents should not send
HTTPS URLs to third-party sites registered as content handlers
without the user's informed consent, for the same reason that user
agents sometimes avoid sending Referer (sic) HTTP headers from secure
sites to third-party sites.
Leaking credentials. User agents must never send username or password information in the URLs that are escaped and included sent to the handler sites. User agents may even avoid attempting to pass to Web-based handlers the URLs of resources that are known to require authentication to access, as such sites would be unable to access the resources in question without prompting the user for credentials themselves (a practice that would require the user to know whether to trust the third-party handler, a decision many users are unable to make or even understand).
This section is non-normative.
A simple implementation of this feature for a desktop Web browser might work as follows.
The registerContentHandler()
method could display a modal dialog box:
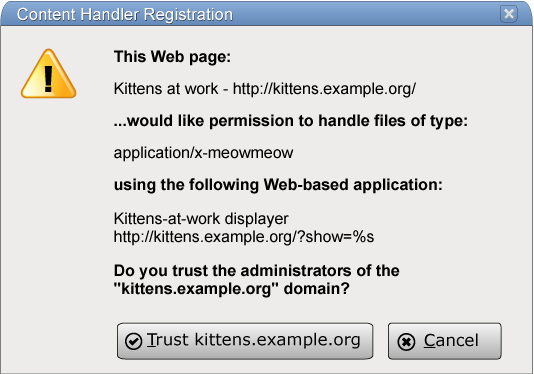
In this dialog box, "Kittens at work" is the title of the page
that invoked the method, "http://kittens.example.org/" is the URL of
that page, "application/x-meowmeow" is the string that was passed to
the registerContentHandler()
method as its first argument (mimeType),
"http://kittens.example.org/?show=%s" was the second argument (url), and "Kittens-at-work displayer" was the third
argument (title).
If the user clicks the Cancel button, then nothing further happens. If the user clicks the "Trust" button, then the handler is remembered.
When the user then attempts to fetch a URL that uses the "application/x-meowmeow" MIME type, then it might display a dialog as follows:
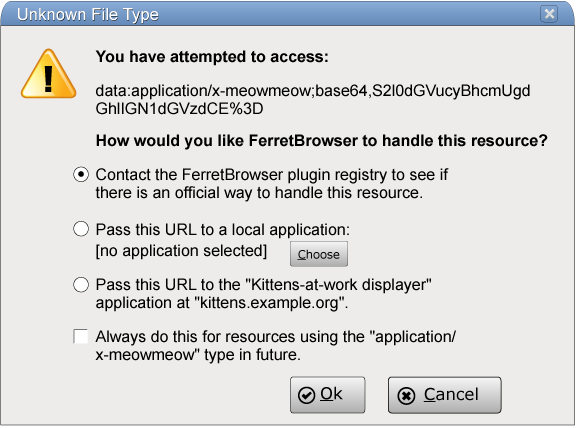
In this dialog, the third option is the one that was primed by the site registering itself earlier.
If the user does select that option, then the browser, in accordance with the requirements described in the previous two sections, will redirect the user to "http://kittens.example.org/?show=data%3Aapplication/x-meowmeow;base64,S2l0dGVucyBhcmUgdGhlIGN1dGVzdCE%253D".
The registerProtocolHandler()
method would work equivalently, but for schemes instead of unknown
content types.
[NoInterfaceObject]
interface NavigatorStorageUtils {
void yieldForStorageUpdates();
};
navigator . yieldForStorageUpdates()If a script uses the document.cookie API, or the
localStorage API, the
browser will block other scripts from accessing cookies or storage
until the first script finishes.
[WEBSTORAGE]
Calling the navigator.yieldForStorageUpdates()
method tells the user agent to unblock any other scripts that may
be blocked, even though the script hasn't returned.
Values of cookies and items in the Storage objects
of localStorage attributes
can change after calling this method, whence its name.
[WEBSTORAGE]
The yieldForStorageUpdates()
method, when invoked, must, if the storage mutex is
owned by the event loop of the task that resulted in the method being
called, release the storage mutex so that it is once
again free. Otherwise, it must do nothing.
External interfaceThe external
attribute of the Window interface must return an
instance of the External interface. The same object
must be returned each time.
interface External {
void AddSearchProvider(DOMString engineURL);
unsigned long IsSearchProviderInstalled(DOMString engineURL);
};
external . AddSearchProvider( url )Adds the search engine described by the OpenSearch description document at url. [OPENSEARCH]
The OpenSearch description document has to be on the same server as the script that calls this method.
external . IsSearchProviderInstalled( url )Returns a value based on comparing url to the URLs of the results pages of the installed search engines.
The url is compared to the URLs of the results pages of the installed search engines using a prefix match. Only results pages on the same domain as the script that calls this method are checked.
Another way of exposing search engines using
OpenSearch description documents is using a link
element with the search link
type.
The AddSearchProvider()
method, when invoked, must run the following steps:
Optionally, abort these steps. User agents may implement the method as a stub method that never does anything, or may arbitrarily ignore invocations with particular arguments for security, privacy, or usability reasons.
Resolve the value of the method's first argument relative to the entry script's base URL.
If this fails, abort these steps.
Process the resulting absolute URL as the URL to an OpenSearch description document. [OPENSEARCH]
The IsSearchProviderInstalled()
method, when invoked, must run the following steps:
Optionally, return 0 and abort these steps. User agents may implement the method as a stub method that never returns a non-zero value, or may arbitrarily ignore invocations with particular arguments for security, privacy, or usability reasons.
If the origin of the entry script is an opaque identifier (i.e. it has no host component), then return 0 and abort these steps.
Let host1 be the host component of the origin of the entry script.
Resolve the scriptURL argument relative to the entry script's base URL.
If this fails, return 0 and abort these steps.
Let host2 be be the <host> component of the resulting absolute URL.
If the longest suffix in the Public Suffix List that matches the end of host1 is different than the longest suffix in the Public Suffix List that matches the end of host2, then return 0 and abort these steps. [PSL]
If the next domain component of host1 and host2 after their common suffix are not the same, then return 0 and abort these steps.
Domain labels must be compared after applying the IDNA ToASCII algorithm to them, with both the AllowUnassigned and UseSTD3ASCIIRules flags set, in an ASCII case-insensitive manner. [RFC3490]
Let search engines be the list of
search engines known by the user agent and made available to the
user by the user agent for which the resulting absolute
URL is a prefix match of the search engine's
URL, if any. For search engines registered using
OpenSearch description documents, the URL of the
search engine corresponds to the URL given in a Url element whose rel
attribute is "results" (the default). [OPENSEARCH]
If search engines is empty, return 0 and abort these steps.
If the user's default search engine (as determined by the user agent) is one of the search engines in search engines, then return 2 and abort these steps.
Return 1.