The W3C held the W3C Social Business Jam from November 8-10, 2011, the W3C's first purely "online" event, in order to explore possible space for standardization to enable the social web for business use-cases. Like any W3C workshop, the Social Business Jam was an online conversation amongst representatives in business, government and technology about the current state of social business and future directions.
The Jam had 1073 unique registrants who attended the Jam. Twenty different industries were represented in the registrant pool, with 57% of the registrants classified their employer as a “large organization”, 20% as a medium organization, 12% as a small organization and 11% were self employed. The Jam let anyone comment on a number of "conversations", which were initiated by a number of invited hosts. An example of a comment is given below:
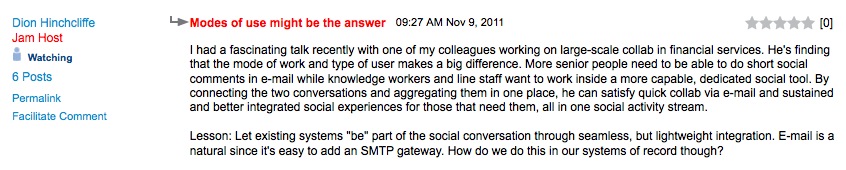
A remark of Dion Hinchcliffe, Dachis Group, in the Jam
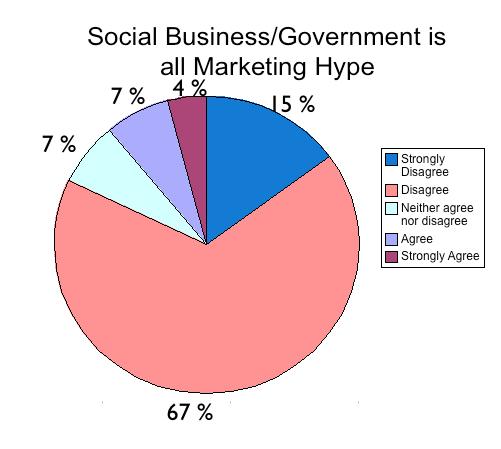
A number of surveys, some mandatory and others optional, were also completed by Jam attendees so the W3C could better understand the strategic landscape around standards for social business. A subset of these surveys will be presented in graphical form throughout the report as follows:
The Jam covered six key aspects of social technology, whose key points are each summarized in their own section.
- Identity Management For Social
- Mobile and Social
- Information Management
- Business Process Meets Social
- Seamless Integration of Social
- Metrics For Social Business
This final report draws conclusions and make specific recommendations for next steps. The primary recommendation is the creation of a community group around these issues. By combing through the Jam data (including poll results, electronic text analysis of the online conversations, and a careful re-reading of key online conversations), several concrete areas have been identified that need the focus of at least a new W3C Community Group focusing on "social business," and possibly a future W3C Business Group and Working Group(s). So join the W3C in taking the next steps!
Identity Management For Social
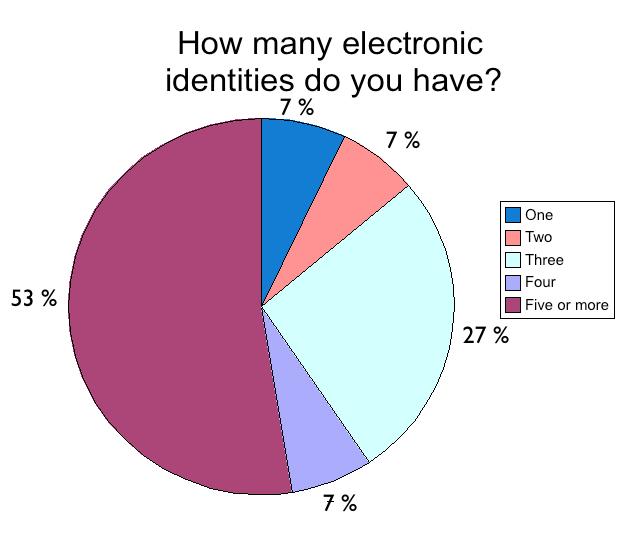
Many people have multiple identities on the Web, with different contractual and legal obligations for professional identities - where the stakes are usually higher - than for personal identities. Yet simply due to self interest, personal identities are often more accurate than corporate identities when it comes to maintaining current personal data such as addresses, phone numbers, name changes and e-mail address updates. Of particular importance is to establish and preserve a separate work and personal identity on a mobile device. Interestingly enough, mobile phone providers are experimenting with virtual machine environments that facilitate separate identities based on the particular virtual machine-in-use. Still, a major barrier in using social technologies in any business is both the lack of integration and secure separation between personal and professional identities, leading to a current "leaky" situation where personal and professional data can mix in the wrong situation just as easily as the right situation.
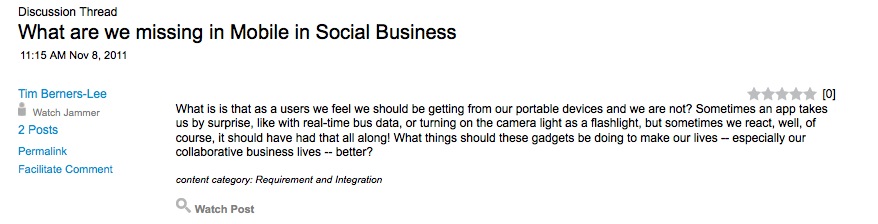
Tim Berners-Lee, Director of W3C, participating in the Jam.
Social technologies should allow multiple and secure identities. In general for identity management, SAML has seen successful adoption inside large enterprises, but it requires pre-trusted environments; this is a major adoption inhibitor in many situations where social interactions may be more dynamic and cross organizational boundaries. In response, there has been some movement towards adopting identity solutions such as OpenID and authorization standards such as OAuth for crossing organizational and security domains. However, the security of the authentication process remain a concern. Another way is to "whitelist" trusted domains via trust frameworks in order to reduce the friction of identity federation. In this model, different identities provide different levels of assurance, where under certain cases a low-assurance identity may be “good enough” (such as "liking" a product), while for other cases (such as high value inter-enterprise collaboration) a higher-level of authentication is needed. This can be aided by two-factor authentication and the upcoming W3C Web Cryptography API.
Mobile and Social
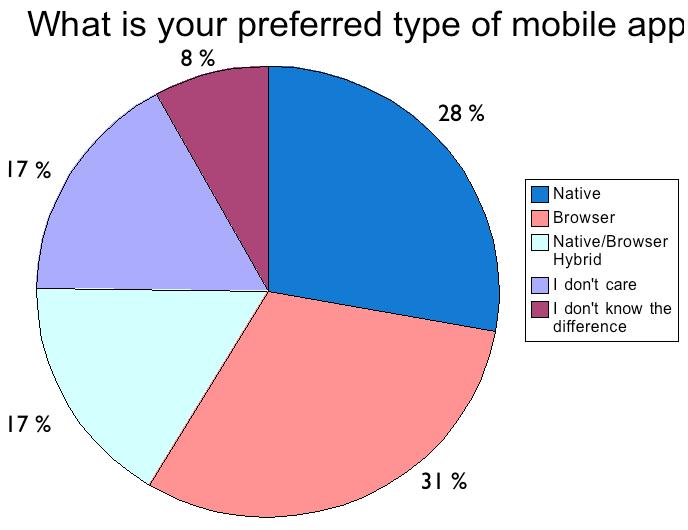
Much of the discussion around mobile devices was around the differences in behavior exhibited by users when using different devices, in particular between truly mobile devices like smart phones and more standard devices like laptops and desktop computers. Unlike traditional computers, mobile phones are viewed as an extension of the person themselves, which creates different behaviors when generating or receiving content.
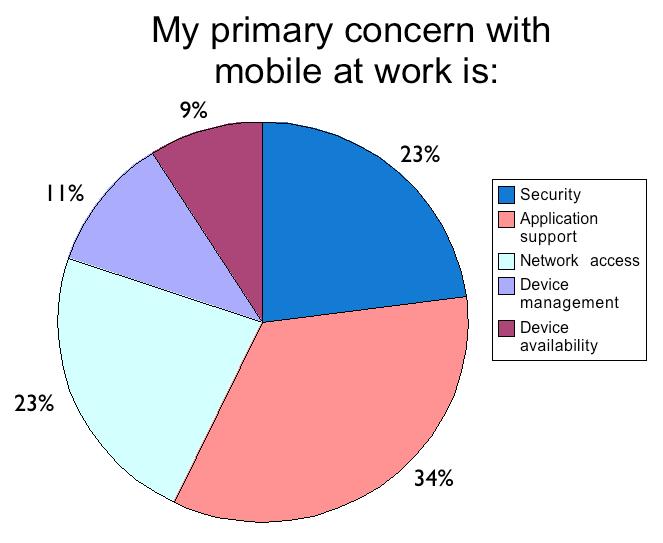
People are much more inclined to generate short-messages and share multimedia content while on "always-on" mobile devices, but also are more likely to be quickly interrupted by mobile phone technologies. Laptops, desktops, and even tablets are less personal and are frequently shared between different users, and so people do not allow interactions with these other sorts of devices to interrupt everyday activity as readily as mobile devices. A mobile phone with a “do not disturb mode” that allows one to concentrate while still connected would be preferred to a phone that has only “off” and “vibrate” modes. This dichotomy between how smart phones are perceived in comparison to other devices led to many other discussions about usage scenarios, including the primary role of smartphone-based geolocation in enabling better co-ordination and serendipity. One of the more innovative ideas was that social activity could be combined with geolocation from mobile devices to automatically install and uninstall applications for users on their mobile devices on as "as-needed" basis.
Information Management
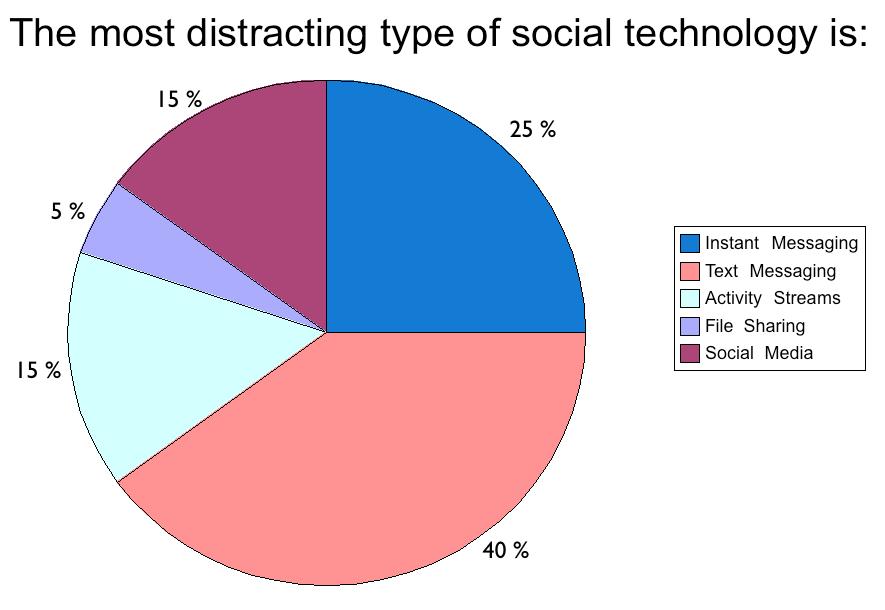
Due to the excessive amount of social data constantly being updated, many people proposed a “social dashboard” to let people centrally integrate various activity streams such as Facebook, Twitter, and their corporate account more effectively. Going beyond "social updates", there was discussion of diverse data “pipes” where any kind of stream of data can be thought of as being capable of being integrated and brought to attention on as "as needed" basis. These streams, also called "pipes", can be applied to the form of social communication which can include e-mail, telephone, status updates, blog postings and "to-do" lists. Yet integrating this data would produce even more data than can be consumed and converted into useful information by a user or organization currently, expanding rather than dealing with a crisis of "data volume". Automated or semi-automated real-time analytics of these streams beneath the "social dashboard" will likely be the way to help with categorizing and prioritizing actions dependent on the social stream, in particular when determining when actions are required within time-frames, such as when determining when there is a "required reading" for a particular meeting.
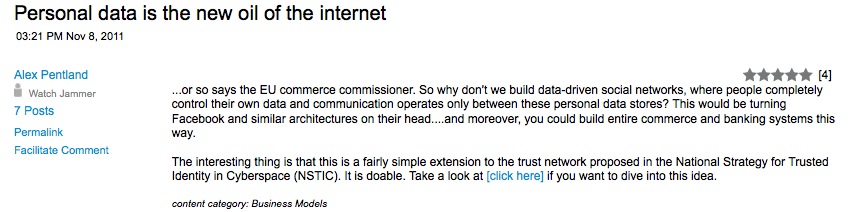
Alex "Sandy" Pentland's comment during Jam
In order to make a "social dashboard" a reality, existing social web platforms need to be integrated, and the OStatus group of draft specifications (ActivityStreams, Portable Contacts, the Salmon Protocol) was considered key to achieving successful social federation and so making a "social dashboard" a reality. However, while currently ActivityStreams are focused on commonly used "verbs" such as share and follow for social activity, more extensions will likely have to be added to let ActivityStreams cover not only human social activity but also machine-generated data. XML-based RSS and Atom feeds as well Semantic Web technologies were mentioned as candidates for the social dashboard, and work would be needed to make such technologies more lightweight and integrated into the increasingly JSON-based world of real-time activity stream communications.
Business Process Meets Social
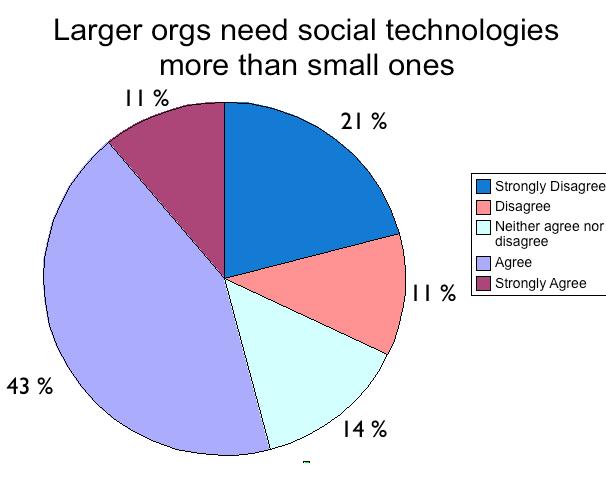
Many of the Jam attendees suggested that BPM based (Business Process Model) processes are often inherently social insofar as they typically describe how a team of people collaboratively achieves a business result. The primary problem with any business process is when exceptions occur, regardless of how structured or unstructured the particular business process is. It seems that social web technologies could be effective at handling exceptions in processes, allowing both quick notification and crowd-sourcing action to deal with the exceptional situation. Participants discussed the fact that social technologies can completely disrupt traditional command-and-control processes, but the social web is necessary to address bottlenecks in existing processes and even foster new and more effective processes. There were divergent views on how to apply social technologies to certain types of business processes and there is clearly much work to be done in learning how to successfully blend business process management tools with free-flowing interactions on the social web. The conversations implied that instant messaging and e-mail were two strong candidates for integration, and further discussion was needed to understand how blogs and file-sharing could also be integrated into business processes as well.
Seamless Integration of Social
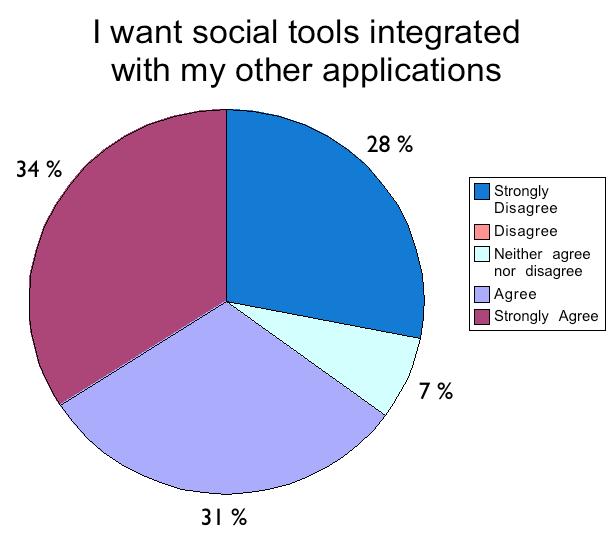
A popular point was around how the roles and importance in organization charts were mismatched to the live social interaction graphs that are generated by social interactions. Organization charts were described as vertical and top down models whereas social graphs were described as horizontal and distributed networks of relationships. These graphs showed where work was actually accomplished rather than just the chain-of-command - and these social graphs could be used across businesses in a number of scenarios ranging from evaluating employees to fostering cross-functional business relationships.
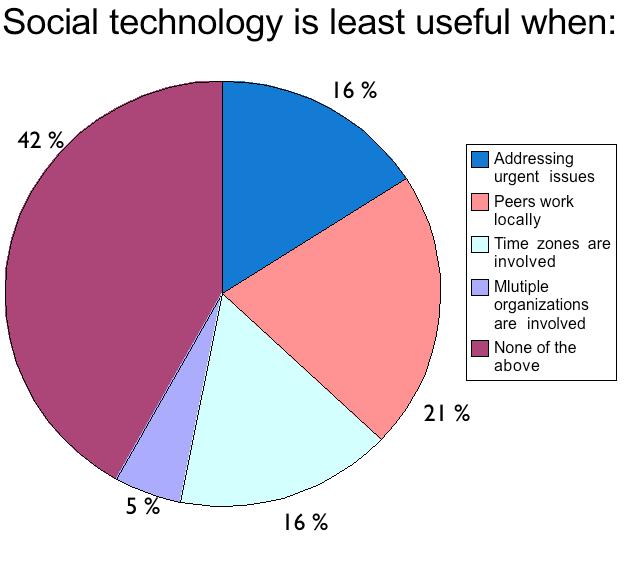
Participants were quick to point out that “social graphs” have matured beyond person-to-person relationships, so that person-to-thing (document, location, web sites, etc.) relationships are growing in number. This could possibly have a strong relationship to the future Internet of Things, where even "things" will be given internet addresses. As the importance of these technologies grow, it leads to further needs by business for what was loosely termed a social platform: a non-monolithic integration of social standards that can integrate social functionality into existing legacy systems. So achieving seamless integration between business applications can be done by relying on a platform that not only provides social capabilities within a particular application but connects the application to the social network “at large” including other social tools (e-mail, instant messaging) via open standards. Again, the strongest candidate for such standards were those being developed around the Federated Social Web community.
Evan Prodromou, co-chair of Federated Social Web XG, at the Jam.
Metrics For Social Business
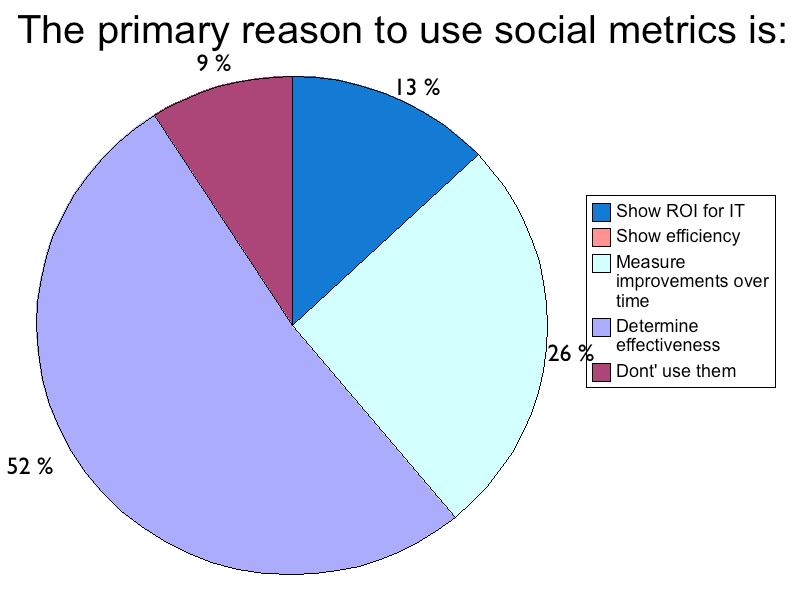
While there is clear value in collecting metrics in order to determine the effectiveness of social technology, clear business objectives are absolutely necessary to provide guidance on precisely what types of metrics are collected. Metrics collected spanned everything from employee moods and conversation topics to hard data on number of users, social network sizes and cycle times. However, there are currently no generally agreed upon techniques for describing metrics once they are collected in a machine-friendly way so thatthey can currently be shared between social systems or analytic systems.
Next Steps
The primary recommendation of the Jam is to form a W3C Social Business Community Group in order to develop a number of customer-driven strategic use-cases for standardizing the Social Web. If necessary, the Social Business Community Group should also create new draft specifications and extensions to existing standards to addresses these use-cases. This group should first continue the analysis of the Jam in more detail, with a focus on defining key terminology such as "integration" and "social platform." The group can also provide coordination and use-cases for various draft specifications developed by other community groups like the Federated Social Web Community Group and push them towards standardization at the W3C or elsewhere.
The Social Business Community Group may transition into a Business Group in order to have more direct co-ordination with other W3C Working Groups (as well as with groups outside the W3C such as IETF Working Groups). If the work started by the Community Group gains enough traction and support across W3C Membership and industry, then the Community Group may wish to transition into a Working Group.
Areas where draft specifications should be developed are as follows:
- Social Business Process: Given that "walled garden" social networks for Business Process Management only create additional integration issues for the rest of the business and exclude those not using BPM tools from discussions, some of the existing Business Process Management standards such as WF-XML, BPEL (BEPL4People, WS-HumanTask, etc.), the proposed Case Management extensions (www.omg.org), and status APIs should be leveraged for effective integration into social platforms, which will likely be built around the OStatus stack.
- Prioritization Extensions for ActivityStreams: ActivityStreams needs a way to mark activities as “required” (where a “required” activity is one that must be opened, read and reviewed by the recipient) as well as a way to deal with prioritization issues in general. Currently, marking activities in an activity stream as “required” is not available through the activity streams specification. Yet prioritization is "user-centric" insofar as an activity required for one person may not be required for another, so the prioritization may be the result of an interaction with a user identity rather than part of the message payload. There are also questions around how to handle a required activity once it has been opened, reviewed, and possibly acted upon by the user, as well as a lack of agreement of how priorities are represented and how to convey priority between different social technologies such as e-mail.
- ActivityStreams Analytics Extensions: Analytics are typically used on the consumer side of social technologies to better understand customer buying habits, interests, web viewing habits, but can be extended to be part of the non-customer side of analytics – helping employees understand and digest activity streams used for running the business. Yet even basic technologies such as text search are insufficient, especially when a user cannot remember specific key words, dates or other details around a conversation. Developing analytics standards on top of ActivityStreams that help users process a “reference library” of social conversations was seen as an important step.
- Social Metric Specification: Metrics were viewed as an essential ingredient in measuring the effectiveness of social technologies, but there is neither consistency in how metric data is represented between various social technologies nor understanding in how this data can be exchanged outside of proprietary solutions; there is little understanding of how to gather and share metrics in a federated social web environment. The scale of metrics, guidelines on how they can be appropriately displayed to users, and how to transmit them need to be explored.
- Social E-Mail Enhancements: Although the web is moving to activity streams, the primary business communication tool of choice is e-mail, and so there are needs to be significantly tighter integration of newer social technologies with e-mail. It was a consensus in among jam participants that e-mail should not be viewed as legacy technology to be replaced by newer social technologies, but that as it is the primary business communication tool of choice, it should be integrated with newer social technologies. So the concept of social e-mail goes beyond embedding widgets or gadgets in a page that shows both activity streams and e-mail, but a truly social mail should allow messages to automatically be converted to and from other social formats depending on the desired medium of communication. The OStatus draft recommendation could be extended to include appropriate interfaces with the SMTP/IMAP/POP standards. Social e-mail should also be a data-source for new draft analytics specifications, allowing for users to more easily reference, share, catalog and analyze e-mails and include e-mail as artifacts in business process and defect tracking systems.
In the final analysis, the Jam was successful in drawing together a large cross-section of industry to discuss the tremendous potential business value of social technologies. Since most business use-cases require deployment both "in" and "outside" corporate firewalls, a federated social web solution that can intercommunicate with existing large social deployments makes sense. Yet the main problem confronting a federated social web is a lack of a common and agreed-upon architecture. While this is at least partially addressed by the OStatus family of specifications, most of these specifications for the most part lack the royalty-free licensing option necessary to encourage large-scale cross-enterprise integration of social web technology and need further work. Therefore, the Social Business Community Group should organize industry around customer-driven use-cases for social technology and then push for a standardized social layer of the Web in order to make social business a reality.