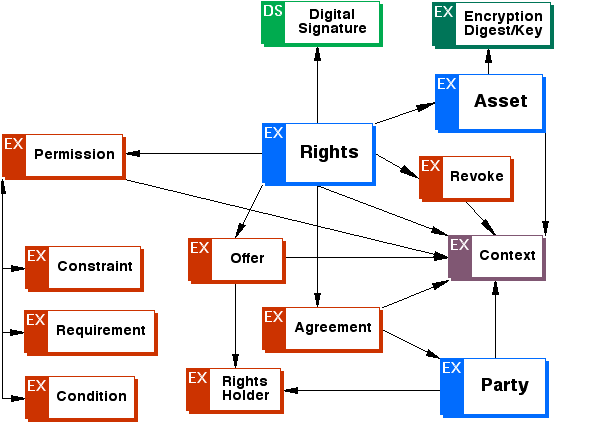
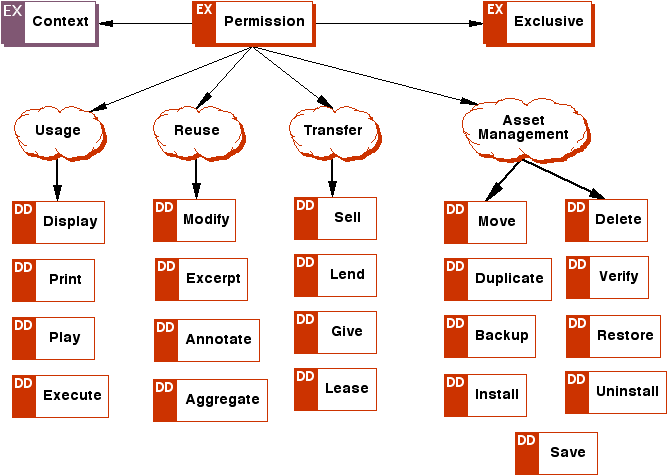
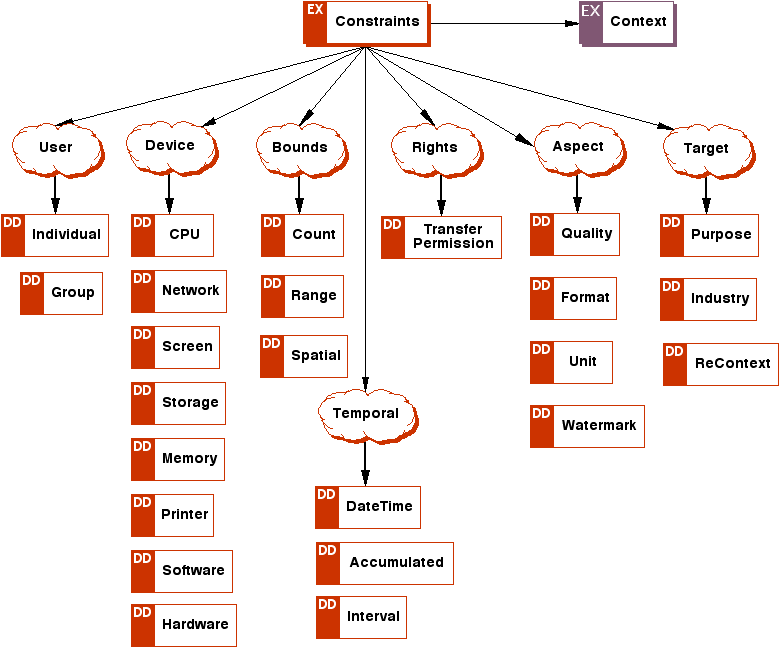
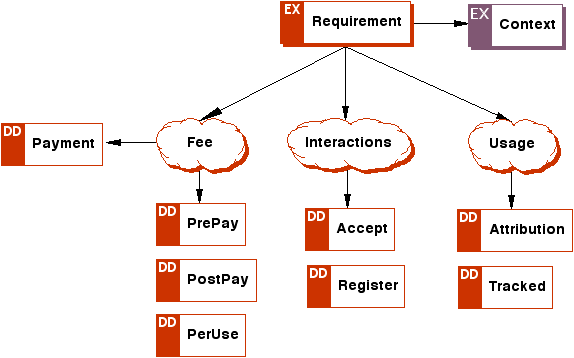
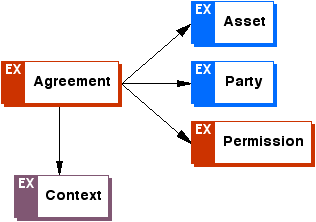
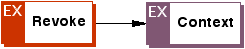
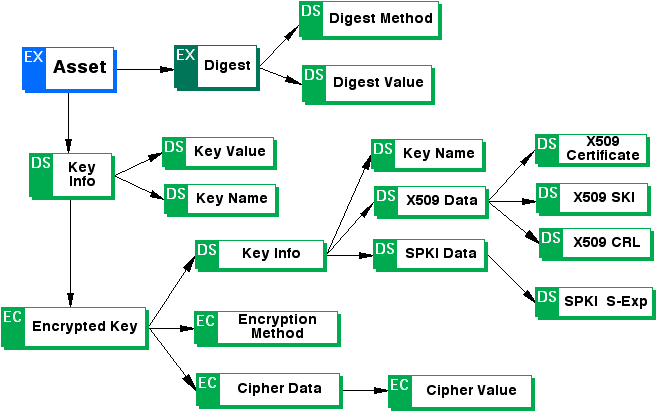
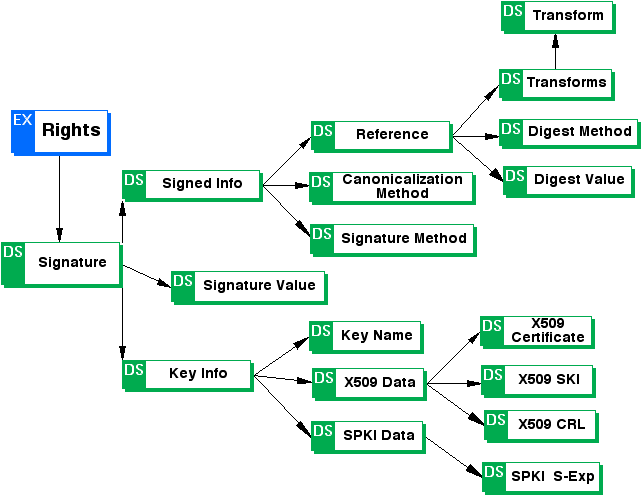
Appendix A: ODRL Expression Language XML Schema (Normative)
The XML Namespace URI for the ODRL Expression Language version 1.1 is:
http://odrl.net/1.1/ODRL-EX
The actual location of the XML Schema is:
http://odrl.net/1.1/ODRL-EX-11.xsd
The XML Schema is documented at:
http://odrl.net/1.1/ODRL-EX-11-DOC/index.html
<?xml version="1.0" encoding="UTF-8"?>
<xsd:schema targetNamespace="http://odrl.net/1.1/ODRL-EX"
xmlns:o-ex="http://odrl.net/1.1/ODRL-EX"
xmlns:xsd="http://www.w3.org/2001/XMLSchema"
xmlns:ds="http://www.w3.org/2000/09/xmldsig#"
xmlns:enc="http://www.w3.org/2001/04/xmlenc#"
elementFormDefault="qualified" attributeFormDefault="qualified" version="1.1">
<xsd:import namespace="http://www.w3.org/2000/09/xmldsig#"
schemaLocation="http://www.w3.org/TR/2002/REC-xmldsig-core-20020212/xmldsig-core-schema.xsd"/>
<!-- NOTE: This URI will be updated as the Encryption specification is advanced -->
<xsd:import namespace="http://www.w3.org/2001/04/xmlenc#"
schemaLocation="http://www.w3.org/Encryption/2001/Drafts/xmlenc-core/xenc-schema.xsd"/>
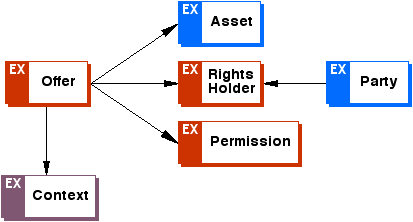
<xsd:element name="rights" type="o-ex:rightsType"/>
<xsd:element name="offer" type="o-ex:offerAgreeType"/>
<xsd:element name="agreement" type="o-ex:offerAgreeType"/>
<xsd:complexType name="offerAgreeType">
<xsd:choice minOccurs="0" maxOccurs="unbounded">
<xsd:element ref="o-ex:context" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:party" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:asset" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:permission" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:constraint" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:requirement" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:condition" minOccurs="0" maxOccurs="unbounded"/>
</xsd:choice>
</xsd:complexType>
<xsd:complexType name="rightsType">
<xsd:complexContent>
<xsd:extension base="o-ex:offerAgreeType">
<xsd:choice minOccurs="0" maxOccurs="unbounded">
<xsd:element ref="o-ex:revoke" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:offer" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:agreement" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="ds:Signature" minOccurs="0"/>
</xsd:choice>
<xsd:attributeGroup ref="o-ex:IDGroup"/>
</xsd:extension>
</xsd:complexContent>
</xsd:complexType>
<xsd:element name="context" type="o-ex:contextType"/>
<xsd:element name="contextElement" abstract="true"/>
<xsd:complexType name="contextType">
<xsd:choice minOccurs="0" maxOccurs="unbounded">
<xsd:element ref="o-ex:context" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:contextElement" minOccurs="0" maxOccurs="unbounded"/>
</xsd:choice>
<xsd:attributeGroup ref="o-ex:IDGroup"/>
</xsd:complexType>
<xsd:complexType name="partyType">
<xsd:choice minOccurs="0" maxOccurs="unbounded">
<xsd:element ref="o-ex:context" minOccurs="0"/>
<xsd:element ref="o-ex:rightsholder" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:party" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:container" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:asset" minOccurs="0" maxOccurs="unbounded"/>
</xsd:choice>
<xsd:attributeGroup ref="o-ex:IDGroup"/>
</xsd:complexType>
<xsd:element name="party" type="o-ex:partyType"/>
<xsd:element name="rightsholder" type="o-ex:rightsHolderType"/>
<xsd:element name="rightsHolderElement" abstract="true"/>
<xsd:complexType name="rightsHolderType">
<xsd:choice minOccurs="0" maxOccurs="unbounded">
<xsd:element ref="o-ex:context" minOccurs="0"/>
<xsd:element ref="o-ex:rightsHolderElement" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:container" minOccurs="0" maxOccurs="unbounded"/>
</xsd:choice>
<xsd:attributeGroup ref="o-ex:IDGroup"/>
</xsd:complexType>
<xsd:complexType name="assetType">
<xsd:choice minOccurs="0" maxOccurs="unbounded">
<xsd:element ref="o-ex:context"/>
<xsd:element ref="o-ex:inherit"/>
<xsd:element name="digest">
<xsd:complexType>
<xsd:choice minOccurs="0" maxOccurs="unbounded">
<xsd:element ref="ds:DigestMethod"/>
<xsd:element ref="ds:DigestValue"/>
</xsd:choice>
</xsd:complexType>
</xsd:element>
<xsd:element ref="ds:KeyInfo"/>
</xsd:choice>
<xsd:attributeGroup ref="o-ex:IDGroup"/>
<xsd:attribute name="type">
<xsd:simpleType>
<xsd:restriction base="xsd:NMTOKEN">
<xsd:enumeration value="work"/>
<xsd:enumeration value="expression"/>
<xsd:enumeration value="manifestation"/>
<xsd:enumeration value="item"/>
</xsd:restriction>
</xsd:simpleType>
</xsd:attribute>
</xsd:complexType>
<xsd:element name="asset" type="o-ex:assetType"/>
<xsd:complexType name="inheritType">
<xsd:choice minOccurs="0" maxOccurs="unbounded">
<xsd:element ref="o-ex:context" minOccurs="0" maxOccurs="unbounded"/>
</xsd:choice>
<xsd:attribute name="override" type="xsd:boolean" default="false"/>
<xsd:attribute name="default" type="xsd:boolean" default="false"/>
</xsd:complexType>
<xsd:element name="inherit" type="o-ex:inheritType"/>
<xsd:element name="permission" type="o-ex:permissionType"/>
<xsd:element name="permissionElement" abstract="true"/>
<xsd:complexType name="permissionType">
<xsd:choice minOccurs="0" maxOccurs="unbounded">
<xsd:element ref="o-ex:context" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:permissionElement" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:container" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:constraint" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:sequence" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:requirement" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:condition" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:asset" minOccurs="0" maxOccurs="unbounded"/>
</xsd:choice>
<xsd:attribute name="exclusive" type="xsd:boolean" use="optional"/>
<xsd:attributeGroup ref="o-ex:IDGroup"/>
</xsd:complexType>
<xsd:element name="constraint" type="o-ex:constraintType"/>
<xsd:element name="constraintElement" abstract="true"/>
<xsd:complexType name="constraintType">
<xsd:choice minOccurs="0" maxOccurs="unbounded">
<xsd:element ref="o-ex:constraint" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:constraintElement" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:container" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:sequence" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:context" minOccurs="0" maxOccurs="unbounded"/>
</xsd:choice>
<xsd:attributeGroup ref="o-ex:IDGroup"/>
<xsd:attribute name="type" type="xsd:anyURI"/>
</xsd:complexType>
<xsd:element name="requirement" type="o-ex:requirementType"/>
<xsd:element name="requirementElement" abstract="true"/>
<xsd:complexType name="requirementType">
<xsd:sequence minOccurs="0" maxOccurs="unbounded">
<xsd:element ref="o-ex:context" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:requirementElement" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:container" minOccurs="0" maxOccurs="unbounded"/>
</xsd:sequence>
<xsd:attributeGroup ref="o-ex:IDGroup"/>
</xsd:complexType>
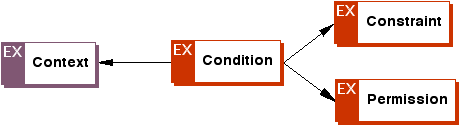
<xsd:element name="condition" type="o-ex:conditionType"/>
<xsd:element name="conditionElement" abstract="true"/>
<xsd:complexType name="conditionType">
<xsd:sequence minOccurs="0" maxOccurs="unbounded">
<xsd:element ref="o-ex:context" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:conditionElement" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:permission" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:constraint" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:container" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:sequence" minOccurs="0" maxOccurs="unbounded"/>
</xsd:sequence>
<xsd:attributeGroup ref="o-ex:IDGroup"/>
</xsd:complexType>
<xsd:complexType name="revokeType">
<xsd:sequence minOccurs="0" maxOccurs="unbounded">
<xsd:element ref="o-ex:context" minOccurs="0" maxOccurs="unbounded"/>
</xsd:sequence>
<xsd:attributeGroup ref="o-ex:IDGroup"/>
</xsd:complexType>
<xsd:element name="revoke" type="o-ex:revokeType"/>
<xsd:complexType name="sequenceType">
<xsd:sequence>
<xsd:element ref="o-ex:seq-item" maxOccurs="unbounded"/>
</xsd:sequence>
<xsd:attribute name="order" default="total">
<xsd:simpleType>
<xsd:restriction base="xsd:NMTOKEN">
<xsd:enumeration value="total"/>
<xsd:enumeration value="partial"/>
</xsd:restriction>
</xsd:simpleType>
</xsd:attribute>
</xsd:complexType>
<xsd:element name="sequence" type="o-ex:sequenceType"/>
<xsd:complexType name="containerType">
<xsd:choice minOccurs="0" maxOccurs="unbounded">
<xsd:element ref="o-ex:container" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:permission" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:permissionElement" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:constraintElement" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:conditionElement" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:requirementElement" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:rightsHolderElement" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:constraint" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:condition" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:sequence" minOccurs="0" maxOccurs="unbounded"/>
</xsd:choice>
<xsd:attribute name="type" default="and">
<xsd:simpleType>
<xsd:restriction base="xsd:NMTOKEN">
<xsd:enumeration value="and"/>
<xsd:enumeration value="in-or"/>
<xsd:enumeration value="ex-or"/>
</xsd:restriction>
</xsd:simpleType>
</xsd:attribute>
<xsd:attributeGroup ref="o-ex:IDGroup"/>
</xsd:complexType>
<xsd:element name="container" type="o-ex:containerType"/>
<xsd:complexType name="seqItemType">
<xsd:choice minOccurs="0" maxOccurs="unbounded">
<xsd:element ref="o-ex:container" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:permission" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:permissionElement" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:constraintElement" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:conditionElement" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:requirementElement" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:rightsHolderElement" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:constraint" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:condition" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="o-ex:sequence" minOccurs="0" maxOccurs="unbounded"/>
</xsd:choice>
<xsd:attribute name="number" type="xsd:integer" use="required"/>
</xsd:complexType>
<xsd:element name="seq-item" type="o-ex:seqItemType"/>
<xsd:attributeGroup name="IDGroup">
<xsd:attribute name="id" type="xsd:ID"/>
<xsd:attribute name="idref" type="xsd:IDREF"/>
</xsd:attributeGroup>
</xsd:schema>
Appendix B: ODRL Data Dictionary XML Schema (Normative)
The XML Namespace URI for the ODRL Data Dictionary version 1.1 is:
http://odrl.net/1.1/ODRL-DD
The actual location of the XML Schema is:
http://odrl.net/1.1/ODRL-DD-11.xsd
The XML Schema is documented at:
http://odrl.net/1.1/ODRL-DD-11-DOC/index.html
<?xml version="1.0" encoding="UTF-8"?>
<xsd:schema targetNamespace="http://odrl.net/1.1/ODRL-DD"
xmlns:o-ex="http://odrl.net/1.1/ODRL-EX"
xmlns:o-dd="http://odrl.net/1.1/ODRL-DD"
xmlns:xsd="http://www.w3.org/2001/XMLSchema"
elementFormDefault="qualified" attributeFormDefault="qualified" version="1.1">
<xsd:import namespace="http://odrl.net/1.1/ODRL-EX"
schemaLocation="http://odrl.net/1.1/ODRL-EX-11.xsd"/>
<!-- Declare all the Permission Elements -->
<xsd:element name="display" type="o-ex:permissionType" substitutionGroup="o-ex:permissionElement"/>
<xsd:element name="print" type="o-ex:permissionType" substitutionGroup="o-ex:permissionElement"/>
<xsd:element name="play" type="o-ex:permissionType" substitutionGroup="o-ex:permissionElement"/>
<xsd:element name="execute" type="o-ex:permissionType" substitutionGroup="o-ex:permissionElement"/>
<xsd:element name="sell" type="o-ex:permissionType" substitutionGroup="o-ex:permissionElement"/>
<xsd:element name="lend" type="o-ex:permissionType" substitutionGroup="o-ex:permissionElement"/>
<xsd:element name="give" type="o-ex:permissionType" substitutionGroup="o-ex:permissionElement"/>
<xsd:element name="lease" type="o-ex:permissionType" substitutionGroup="o-ex:permissionElement"/>
<xsd:element name="modify" type="o-ex:permissionType" substitutionGroup="o-ex:permissionElement"/>
<xsd:element name="excerpt" type="o-ex:permissionType" substitutionGroup="o-ex:permissionElement"/>
<xsd:element name="aggregate" type="o-ex:permissionType" substitutionGroup="o-ex:permissionElement"/>
<xsd:element name="annotate" type="o-ex:permissionType" substitutionGroup="o-ex:permissionElement"/>
<xsd:element name="move" type="o-ex:permissionType" substitutionGroup="o-ex:permissionElement"/>
<xsd:element name="duplicate" type="o-ex:permissionType" substitutionGroup="o-ex:permissionElement"/>
<xsd:element name="delete" type="o-ex:permissionType" substitutionGroup="o-ex:permissionElement"/>
<xsd:element name="verify" type="o-ex:permissionType" substitutionGroup="o-ex:permissionElement"/>
<xsd:element name="backup" type="o-ex:permissionType" substitutionGroup="o-ex:permissionElement"/>
<xsd:element name="restore" type="o-ex:permissionType" substitutionGroup="o-ex:permissionElement"/>
<xsd:element name="install" type="o-ex:permissionType" substitutionGroup="o-ex:permissionElement"/>
<xsd:element name="uninstall" type="o-ex:permissionType" substitutionGroup="o-ex:permissionElement"/>
<xsd:element name="save" type="o-ex:permissionType" substitutionGroup="o-ex:permissionElement"/>
<!-- Declare the Payment Element (used in Requirements) -->
<xsd:element name="payment">
<xsd:complexType>
<xsd:sequence>
<xsd:element name="amount">
<xsd:complexType>
<xsd:simpleContent>
<xsd:extension base="xsd:decimal">
<xsd:attribute name="currency" type="xsd:NMTOKEN" use="required"/>
</xsd:extension>
</xsd:simpleContent>
</xsd:complexType>
</xsd:element>
<xsd:element name="taxpercent" minOccurs="0">
<xsd:complexType>
<xsd:simpleContent>
<xsd:extension base="xsd:decimal">
<xsd:attribute name="code" type="xsd:NMTOKEN" use="required"/>
</xsd:extension>
</xsd:simpleContent>
</xsd:complexType>
</xsd:element>
</xsd:sequence>
</xsd:complexType>
</xsd:element>
<!-- Define the dataTypes used for Requirements that use Payment element -->
<xsd:complexType name="feeType">
<xsd:complexContent>
<xsd:extension base="o-ex:requirementType">
<xsd:sequence>
<xsd:element ref="o-dd:payment"/>
</xsd:sequence>
</xsd:extension>
</xsd:complexContent>
</xsd:complexType>
<!-- Declare all the Requirements Elements -->
<xsd:element name="prepay" type="o-dd:feeType" substitutionGroup="o-ex:requirementElement"/>
<xsd:element name="postpay" type="o-dd:feeType" substitutionGroup="o-ex:requirementElement"/>
<xsd:element name="peruse" type="o-dd:feeType" substitutionGroup="o-ex:requirementElement"/>
<xsd:element name="accept" type="o-ex:requirementType" substitutionGroup="o-ex:requirementElement"/>
<xsd:element name="register" type="o-ex:requirementType" substitutionGroup="o-ex:requirementElement"/>
<xsd:element name="attribution" type="o-ex:requirementType" substitutionGroup="o-ex:requirementElement"/>
<xsd:element name="tracked" type="o-ex:requirementType" substitutionGroup="o-ex:requirementElement"/>
<!-- Declare all the RightsHolder Elements -->
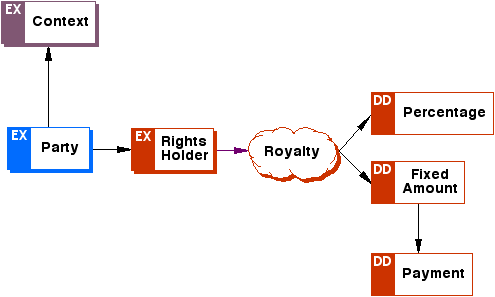
<xsd:element name="fixedamount" substitutionGroup="o-ex:rightsHolderElement">
<xsd:complexType>
<xsd:complexContent>
<xsd:extension base="o-ex:rightsHolderType">
<xsd:sequence>
<xsd:element ref="o-dd:payment"/>
</xsd:sequence>
</xsd:extension>
</xsd:complexContent>
</xsd:complexType>
</xsd:element>
<xsd:element name="percentage" substitutionGroup="o-ex:rightsHolderElement">
<xsd:simpleType>
<xsd:restriction base="xsd:decimal">
<xsd:minInclusive value="0"/>
<xsd:maxInclusive value="100"/>
</xsd:restriction>
</xsd:simpleType>
</xsd:element>
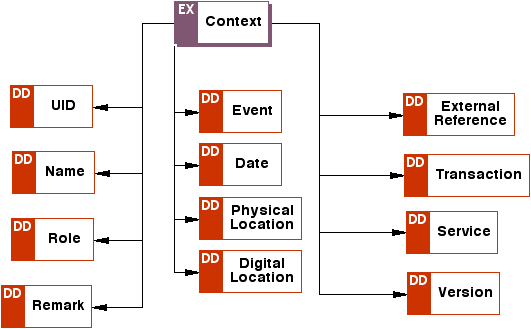
<!-- Declare all the Context Elements -->
<xsd:simpleType name="uriAndOrString">
<xsd:union memberTypes="xsd:anyURI xsd:string"/>
</xsd:simpleType>
<xsd:element name="uid" type="o-dd:uriAndOrString" substitutionGroup="o-ex:contextElement"/>
<xsd:element name="role" type="xsd:anyURI" substitutionGroup="o-ex:contextElement"/>
<xsd:element name="name" type="xsd:string" substitutionGroup="o-ex:contextElement"/>
<xsd:element name="remark" type="xsd:string" substitutionGroup="o-ex:contextElement"/>
<xsd:element name="event" type="xsd:string" substitutionGroup="o-ex:contextElement"/>
<xsd:element name="pLocation" type="xsd:string" substitutionGroup="o-ex:contextElement"/>
<xsd:element name="dLocation" type="xsd:anyURI" substitutionGroup="o-ex:contextElement"/>
<xsd:element name="reference" type="xsd:anyURI" substitutionGroup="o-ex:contextElement"/>
<xsd:element name="version" type="xsd:string" substitutionGroup="o-ex:contextElement"/>
<xsd:element name="transaction" type="xsd:string" substitutionGroup="o-ex:contextElement"/>
<xsd:element name="service" type="xsd:anyURI" substitutionGroup="o-ex:contextElement"/>
<xsd:element name="date" type="o-dd:dateType" substitutionGroup="o-ex:contextElement"/>
<!-- Declare all the Constraint Elements -->
<xsd:element name="individual" type="o-ex:constraintType" substitutionGroup="o-ex:constraintElement"/>
<xsd:element name="group" type="o-ex:constraintType" substitutionGroup="o-ex:constraintElement"/>
<xsd:element name="cpu" type="o-ex:constraintType" substitutionGroup="o-ex:constraintElement"/>
<xsd:element name="network" type="o-ex:constraintType" substitutionGroup="o-ex:constraintElement"/>
<xsd:element name="screen" type="o-ex:constraintType" substitutionGroup="o-ex:constraintElement"/>
<xsd:element name="storage" type="o-ex:constraintType" substitutionGroup="o-ex:constraintElement"/>
<xsd:element name="memory" type="o-ex:constraintType" substitutionGroup="o-ex:constraintElement"/>
<xsd:element name="printer" type="o-ex:constraintType" substitutionGroup="o-ex:constraintElement"/>
<xsd:element name="software" type="o-ex:constraintType" substitutionGroup="o-ex:constraintElement"/>
<xsd:element name="hardware" type="o-ex:constraintType" substitutionGroup="o-ex:constraintElement"/>
<xsd:element name="spatial" type="o-ex:constraintType" substitutionGroup="o-ex:constraintElement"/>
<xsd:element name="quality" type="o-ex:constraintType" substitutionGroup="o-ex:constraintElement"/>
<xsd:element name="format" type="o-ex:constraintType" substitutionGroup="o-ex:constraintElement"/>
<xsd:element name="unit" type="o-ex:constraintType" substitutionGroup="o-ex:constraintElement"/>
<xsd:element name="watermark" type="o-ex:constraintType" substitutionGroup="o-ex:constraintElement"/>
<xsd:element name="purpose" type="o-ex:constraintType" substitutionGroup="o-ex:constraintElement"/>
<xsd:element name="industry" type="o-ex:constraintType" substitutionGroup="o-ex:constraintElement"/>
<xsd:element name="count" type="xsd:positiveInteger" substitutionGroup="o-ex:constraintElement"/>
<xsd:element name="range" substitutionGroup="o-ex:constraintElement">
<xsd:complexType>
<xsd:complexContent>
<xsd:extension base="o-ex:constraintType">
<xsd:sequence>
<xsd:element name="min" type="xsd:decimal" minOccurs="0"/>
<xsd:element name="max" type="xsd:decimal" minOccurs="0"/>
</xsd:sequence>
</xsd:extension>
</xsd:complexContent>
</xsd:complexType>
</xsd:element>
<xsd:element name="datetime" type="o-dd:dateType" substitutionGroup="o-ex:constraintElement"/>
<xsd:simpleType name="dateAndOrTime">
<xsd:union memberTypes="xsd:date xsd:dateTime"/>
</xsd:simpleType>
<xsd:complexType name="dateType">
<xsd:complexContent>
<xsd:extension base="o-ex:constraintType">
<xsd:choice>
<xsd:sequence>
<xsd:element name="start" type="o-dd:dateAndOrTime" minOccurs="0"/>
<xsd:element name="end" type="o-dd:dateAndOrTime" minOccurs="0"/>
</xsd:sequence>
<xsd:element name="fixed" type="o-dd:dateAndOrTime" minOccurs="0"/>
</xsd:choice>
</xsd:extension>
</xsd:complexContent>
</xsd:complexType>
<xsd:element name="accumulated" type="xsd:duration" substitutionGroup="o-ex:constraintElement"/>
<xsd:element name="interval" type="xsd:duration" substitutionGroup="o-ex:constraintElement"/>
<xsd:element name="recontext" type="xsd:boolean" substitutionGroup="o-ex:constraintElement"/>
<!-- Transfer Permission is defined as a ContainerType to enable complete expression of
rights in the Constraint -->
<xsd:element name="transferPerm" substitutionGroup="o-ex:container">
<xsd:complexType>
<xsd:complexContent>
<xsd:extension base="o-ex:containerType">
<xsd:attribute name="downstream" default="equal">
<xsd:simpleType>
<xsd:restriction base="xsd:NMTOKEN">
<xsd:enumeration value="equal"/>
<xsd:enumeration value="less"/>
<xsd:enumeration value="notgreater"/>
</xsd:restriction>
</xsd:simpleType>
</xsd:attribute>
</xsd:extension>
</xsd:complexContent>
</xsd:complexType>
</xsd:element>
</xsd:schema>