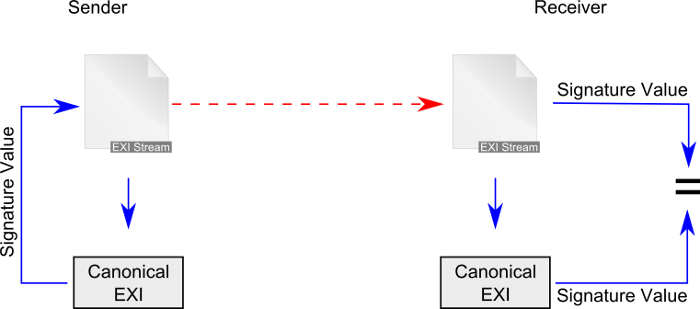
The subsequently described EXI Canonicalization steps and algorithms expect as input
EXI events
(e.g., SE, NS, and AT events). The input MUST be a sequence of EXI events and
produces as output a canonicalized EXI body stream. Following the presented
algorithms guarantees that logically-identical documents produce identical
serialized EXI Body stream representations (assuming the same EXI coding options).
3.1 EXI Alignment Options and Streams
EXI provides four alignment options, namely bit-packed,
byte-alignment, pre-compression, and
compression.
The canonicalized EXI form is the resulting EXI stream following the rules
defined in this document. When the alignment option compression is
set for an EXI stream, its canonical form is computed as if the EXI stream was
encoded using the alignment option pre-compression.
EXI processors may make use of padding bits, for example to make the length of
the EXI stream byte-aligned. In a Canonical EXI stream padding bits, if
necessary, MUST always be represented as a sequence of 0 (zero) bits.
3.2 EXI Event Selection
EXI processors represent a given event such as a start element or an attribute
by serializing an event code first, followed by the according event content.
Each event code is represented by a sequence of 1 to 3 parts that uniquely
identifies an event.
In situations where EXI grammars provide more than one possible event (-code)
the canonical EXI form prescribes which event and respectively which event code
has to be chosen. That said, it is not uncommon that an EXI processors has
certain flexibility in choosing the appropriate EXI grammar production, or
respectively the appropriate event.
Canonical EXI processors MUST follow a three step process for selecting the one
valid event(-code).
3.2.2 Prune productions for non applicable events with content values
In the case of an attribute (AT) or a character (CH) event, productions MUST
be pruned that cannot be used to represent the content value according to
the associated EXI datatype (e.g., the content value "abc" cannot be
represented with the the EXI Integer datatype).
3.2.3 Use the event with the most accurate event
After excluding productions that are not usable (according to the convention
in use or according to the EXI datatype) a canonical EXI processor MUST
follow the subsequent order:
Use the event with the most accurate event content first
For Start Element events the order is as follows:
SE( qname )
SE ( uri : * )
SE ( * )
For Attribute events the order is as follows:
AT( qname )
AT ( uri : * )
AT ( * )
IF the accurateness is the same use the event with the least event
code parts
Further, a value content item that can be represented by the associated EXI
datatype MUST be represented with the associated datatype representation.
When the strict option is false, attributes and character events that
cannot be represented by the associated EXI datatype representations (e.g.,
schema-invalid values) MUST use the additional untyped AT and CH terminal
symbols.
Note:
A Canonical EXI processor MUST NOT account for XML schema validity (just
like an EXI processor). The verification solely bases on EXI grammars
and EXI datatypes.
The appendix section B.1 EXI Event Selection depicts one
concrete example for choosing the correct event.
3.3 EXI Stream Order
In general, a canonical EXI processor SHALL NOT change the order of the EXI input
sequence. The only exceptions to this statement are sequences of attributes
and/or namespace declarations.
The EXI specification defines that namespace (NS) and attribute (AT) events
associated with a given element occur directly after the start element (SE)
event in the following order:
| NS | NS | ... | NS | AT (xsi:type) | AT (xsi:nil) | AT | AT | ... | AT |
In addition, canonical EXI specifies that namespace declarations for a given
element MUST be sorted lexicographically according to the NS prefix. Further,
canonical EXI strictly requires that an xsi:type or an xsi:nil attribute MUST
occur before other AT events even if it does not impact grammar selection.
Moreover, attributes other than xsi:type and xsi:nil for a given element MUST be
sorted lexicographically, first by qname local-name then by qname uri.
Note:
Optimizations such as pruning insignificant xsi:type values
(e.g., xsi:type="xsd:string" for string values) or
insignificant xsi:nil values (e.g.,
xsi:nil="false") is prohibited for a Canonical EXI
processor.
3.4 EXI Datatypes
This section describes the built-in EXI datatype representations used for
representing content items in canonical EXI streams.
When the
Preserve.lexicalValues option is true, individual items are
represented as String. Each value MUST be represented as a String with the
associated restricted character set, if such a set is defined for the associated
datatype representation (see Restricted
Character Sets for Built-in EXI Datatype Representations). String
content items associated with a restricted character MUST also follow the rules
described in 3.4.7 Restricted Character Sets.
When the
Preserve.lexicalValues option is false, a value content item MUST
be represented with the associated datatype representation. The following
sub-sections describe the Canonical EXI behavior for datatypes that otherwise
may not lead to a uniquely defined representation.
EXI 1.0 permits the use of untyped AT or CH terminal symbols to represent a value
content item even when a typed AT or CH terminal symbol is available that could
have been used to represent the value. Therefore, given an input value content
item that uses an untyped AT or CH terminal symbol despite the availability of a
typed alternative terminal symbol, it is not apparent whether the use of the
untyped terminal symbol was due to the result of observing the event selection
rule described in Section 3.2 EXI Event Selection or otherwise (i.e.
negligence of observing the rule) unless switching to the typed alternative
terminal symbol is actually attempted by a Canonical EXI processor. To cope with
this situation, Canonical EXI processors SHOULD be able to convert an untyped
value into each of the datatype representations defined in EXI 1.0 as long as
the target datatype representation can accept the value.
3.4.1 Unsigned Integer
The EXI specification defines that the Unsigned
Integer datatype representation supports unsigned integer
numbers of arbitrary magnitude. EXI processors SHOULD support arbitrarily
large Unsigned Integer values. EXI processors MUST support Unsigned Integer
values less than 2147483648.
Canonical EXI processors MUST use the Unsigned Integer datatype
representation even if a value goes beyond the value 2147483647.
3.4.2 Enumeration
The EXI
Enumeration assigns to each item an unsigned integer value
that corresponds to its ordinal position in the enumeration in schema-order
starting with position zero. When there is more than one item that
represents the same value in the enumeration, the value MUST be represented
by using the first ordinal position that represents the value.
3.4.3 Decimal
The EXI
Decimal datatype is a Boolean sign followed by two Unsigned
Integers. A sign value of zero (0) is used to represent positive Decimal
values and a sign value of one (1) is used to represent negative Decimal
values. The first Unsigned Integer represents the integral portion of the
Decimal value. The second Unsigned Integer represents the fractional portion
of the Decimal value with the digits in reverse order to preserve leading
zeros.
The canonical EXI Decimal MUST respect the following constraint.
3.4.4 Float
The EXI
Float datatype uses two consecutive EXI Integers.
The first Integer represents the mantissa of the floating point number and
the second Integer represents the base-10 exponent of the floating point
number.
The canonical EXI Float MUST respect the following constraints.
A mantissa value of -0 MUST be changed to 0. If the mantissa is 0,
then the exponent MUST be 0. If the mantissa is not 0, mantissas
MUST have no trailing zeros.
An exponent value of -0 MUST be changed to 0.
Given an EXI Float value that consists of one integer representing its
mantissa and the other integer representing its exponent, Canonical EXI
processors MUST find an equivalent canonical EXI Float that satisfies the
above constraints, where the rules of determining equivalence is described
below.
Two floats A and B each denoted as (mantissa, exponent) pair of (mA, eA) and
(mB, eB) where eA >= eB are equivalent under the following circumstances.
Both mantissa and exponent are the same between the two floats.
Otherwise, if two exponents are different (i.e. eA > eB), substitute
A with A2 where A2 has exponent eB and mantissa mA *
10(eA-eB). If A2 and B are equivalent per the rule 1
above, A and B are equivalent.
The appendix section B.3 EXI Floats depicts one example
algorithm for finding the canonical EXI Float that is equivalent to a given
EXI Float value.
3.4.6 String and String Table
The EXI String datatype representation is a length prefixed sequence of
characters. If no restricted character set is defined for the string, each
character is represented by its Unicode code point. The Unicode standard
allows multiple different representations of certain characters. A canonical
EXI processor MUST NOT change the code points.
Further, a String value MUST be represented as string value hit if possible.
Unless the convention used by the application dictates differently (e.g.,
EXI Profile parameter localValuePartitions set to "0"). EXI processors MUST
first try to represent the string value as local hit and only when this is
not successful as global value hit.
Note:
A String value miss MAY also need to follow the rules described in
3.4.7 Restricted Character Sets according to the given restricted character
set, if available.
Note that a Canonical EXI processor MUST also respect the XML schema
whiteSpace facet, if available.
3.4.7 Restricted Character Sets
Restricted
Character Sets in EXI enable to restrict the characters of
the string datatype. The canonical representation dictates that characters
from the restricted character set MUST use the according n-bit
Unsigned Integer. Hence, only characters that are not in the set SHALL be
represented by the n-bit Unsigned Integer N followed by the
Unicode code point of the character represented as an Unsigned Integer.
3.4.8 Datatype Representation Map
The EXI option datatypeRepresentationMap may specify an alternate set of
datatype representations for typed values in the EXI body stream. This
specification does not define any canonicalization rules for alternate
representations. Other specifications and/or groups making use of this
feature MAY describe a canonical form.