This section covers details about each step in the authentication process.
3.2.3 Processing the WebID Profile
A Verification Agent must be able to process documents in RDF/XML [RDF-SYNTAX-GRAMMAR] and XHTML+RDFa [XHTML-RDFA]. A server responding to a WebID Profile request should be able to deliver at least RDF/XML or RDFa. The Verification Agent must set the Accept-Header to request application/rdf+xml with a higher priority than text/html and application/xhtml+xml. If the server answers such a request with an HTML representation of the resource, this should describe the WebId Profile with RDFa.
This section will explain how a Verification Agent extracts semantic data describing the identification credentials from a WebID Profile.
3.2.4 Verifying the WebID is identified by that public key
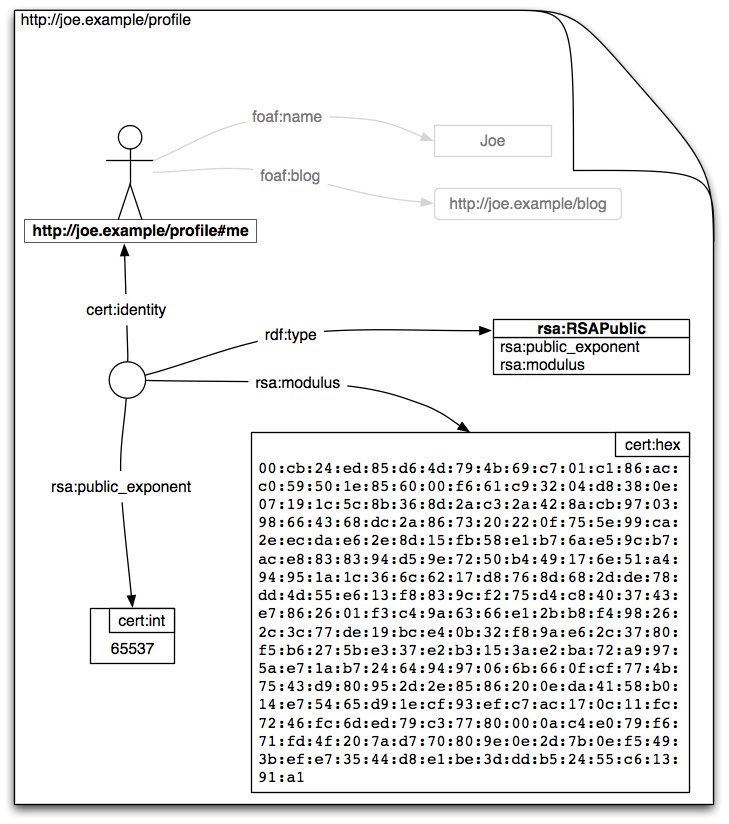
The Verification Agent must check that the WebID Profile associates the WebID with the public key given in the X.509 Certificate. There are number of ways of doing this, each of which essentially consists in checking that the graph of relations in the Profile contain a pattern of relations.
Assuming the public key is an RSA key, and that its modulus is "9D79BFE2498..." and exponent "65537" then the query to ask the graph is
PREFIX cert: <http://www.w3.org/ns/auth/cert#>
PREFIX rsa: <http://www.w3.org/ns/auth/rsa#>
ASK {
[] cert:identity <http://example.org/webid#public>;
rsa:modulus "9D79BFE2498..."^^cert:hex;
rsa:public_exponent "65537"^^cert:int .
}
If the query returns true, then the graph has validated the associated public key with the WebID.
The above requires the graph to be able to do inferencing on dataytypes. This is because people may publish their modulus string in a number of syntactical ways. The modulus can be colon seperated, spread over a number of lines, or contain arbitrary non hex characters such as "9D ☮ 79 ☮ BF ☮ E2 ☮ F4 ☮ 98 ☮..." . The datatype itself need not necessarily be expressed in cert:hex, but could use a number of xsd integer datatype notations, cert:int or future base64 notations.
Should we define the base64 notation?
If a Verifying Agent does not have access to a literal inferencing engine, then the modulus should be extracted from the graph, normalised into a big integer (integers without an upper bound), and compared with the values given in the public key certificate. After replacing the ?webid variable in the following query with the required value the Verifying Agent can query the Profile Graph with
PREFIX cert: <http://www.w3.org/ns/auth/cert#>
PREFIX rsa: <http://www.w3.org/ns/auth/rsa#>
SELECT ?m ?e
WHERE {
[] cert:identity ?webid ;
rsa:modulus ?m ;
rsa:public_exponent ?e .
}
Here the verification agent must check that one of the answers for ?m and ?e matches the integer values of the modulus and exponent given in the public key in the certificate.
The public key could be a DSA key. We need to add an ontology for DSA too. What other cryptographic ontologies should we add?