The existing WWW infrastructure already provides for authentication of web sites. Unfortunately, the advent of phishing has shown that the mainstream user interface to web site authentication is not meaningful to users. This paper proposes a new browser user interface widget, the petname tool, that integrates meaningful authentication information into the browsing workflow.
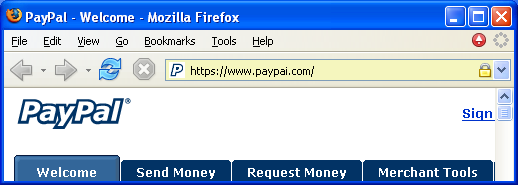
From the user's perspective, a phishing attack targeting ABC.com customers is readily detected if the user has no relationship with ABC.com. On the other hand, the attack poses a real danger if the user does have a relationship with ABC.com. Should the deception succeed, the user will treat requests coming from the phisher as if they had come from ABC.com. To avoid this dire fate, the user must be able to readily identify the relationship relevant to the current request. To this end, this paper proposes the petname tool. Consider the screenshots below:

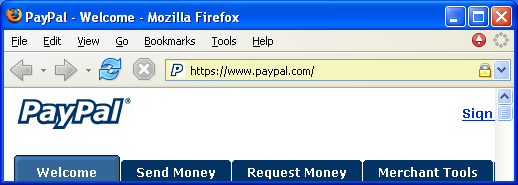
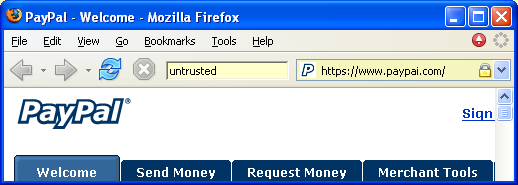
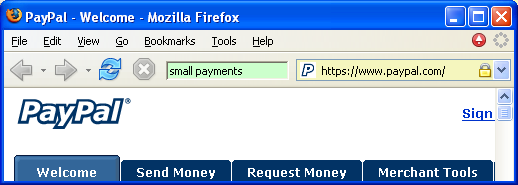
The above spoofing attack reveals a fundamental shortcoming in the mainstream web browser UI. The web page; the URL; the SSL certificate (if any); indeed, all information displayed to the user; is information chosen by the attacker. The user is then asked to discover discrepancies in information that has been carefully designed for deception. This type of game is better suited to a book of puzzles than a secure user interface.
The petname tool sits in the web browser's toolbar, alongside other tools like the Address bar. Using the petname tool, the user can save a reminder note about a relationship he has with a secure site. The petname tool will then automatically display this reminder note every time he visits the site. After following a hyperlink, the user need only check that the expected reminder note is being displayed in the petname tool. If so, he can be sure he is using the same site he has in the past.
The visited web site has no opportunity to determine the contents of the petname tool. The information displayed by the petname tool is provided solely by the user. This crucial property differentiates the petname tool from all other tools in the mainstream web browser UI. The user now has a reference to consult, free from possible deception by the visited web site.
The petname tool has three states.

The current page did not come from an SSL site. Anyone could have produced the page's content. Anyone could receive any information you enter into the page. You should treat the current page as you would a stranger.

The current page came from an SSL site that you do not have a relationship with. Anyone could have produced the page's content. You should treat the current page as you would a stranger.
If you decide to form a new relationship with the site, overwrite the contents of the petname tool with a reminder note describing the new relationship. This reminder note will be displayed in the petname tool every time you return to the site.

The current page came from an SSL site that you have a relationship with. Use the displayed petname to remember the nature of your relationship and proceed accordingly. As you gain experience with the site, update your petname to reflect the evolving relationship.
When the user creates a new petname, the petname tool creates a new bookmark to the current page. The "Name" field of the bookmark is the user chosen petname. The "Description" field of the bookmark contains the hash of the CA's public key and the subject's O, L, ST and C certificate fields. If the subject has no O (Organization) field, the CN (domain name) field is used instead. On each page transition, the petname tool looks at the certificate chain of the SSL connection that delivered the page and searches for a corresponding bookmark. If one is found, the petname field is populated with the bookmark's "Name". Otherwise, the petname field is populated with the string "untrusted".
The petname tool uses the CA (Certificate Authority) and subject DN (Distinguished Name) as the secure identifier for a relationship because many secure sites use multiple domain names and multiple public keys. Further, it is important that sites be able to replace key pairs without breaking their user's petnames.
You receive an email that purports to be from your bank. The email alerts you of a pending task that you must attend to. A hyperlink to the relevant page at the bank's web site is provided. You follow the hyperlink and arrive at a web page that looks like a page from your bank's web site. Should you proceed with the request or not?
If the petname tool is not displaying the reminder note you've associated with your bank, the email is likely a fraud. Use your petname bookmark to access your bank's web site and report the attack.
If the petname tool is displaying the expected reminder note, the current web page is from your bank's web site.
The petname tool is an anti-phishing solution that requires no changes to WWW servers, WWW content, CAs, or underlying browser infrastructure. The tool has been implemented as a small browser addon. The security of this addon does depend upon the browser providing some form of trusted path UI. For example, the browser window may have reserved screen real estate for the browser toolbar, and/or may color the toolbar background with an unguessable tartan. These measures prevent a phisher from spoofing the petname tool itself.
By itself, the petname tool provides an easy to use display and tracking of a user's relationships; however, in haste, a user may neglect to check the petname tool before proceeding with a request. A further step would be to bind authorization tokens, such as passwords, to the cryptographic designator of the site they should be submitted to.
For example, the browser's password manager should generate passwords on behalf of the user and autofill login forms with the user's username and password. The algorithm to determine the login information should be similar to that used by the petname tool. In particular, the same cryptographic identifier for the remote site should be used to determine which password to autofill.
Given a password manager like the one described above, the user will never type in a password, or even know a password. The browser is completely responsible for managing the exchange of authorization tokens with remote sites. Under this regime, the hasty user cannot be phished for a password. The petname tool is still a necessary tool in this setup, since passwords are not the only valuable secrets. The user still must check the petname tool before entering other secrets, such as his SSN, credit card number, etc. More generally, the user needs to know which of his known correspondents is presenting the information displayed in a web page.
Using only a small addon to the mainstream browser UI, the petname tool provides a strong defense against phishing. The proposed user interface is as simple as the creation of a bookmark and yet provides a defense that cannot be undermined without subverting the browser itself.
As presented here, the petname tool provides strong protection for existing relationships, but does not assist with the creation of new relationships. Similar techniques can be used to secure the process of introducing a user to a new entity.
The petname tool is based on naming theory developed in the capability-based security community. This theory finds its origins in work done by Mark Miller and others working at Electric Communities at the time. The author thanks the members of the cap-talk mailing list for their input into the development of the petname tool.