Translating EPAL to P3P
- How to keep enterprise privacy promises in sync with the actual
practices
Matthias Schunter, Els Van Herreweghen, Michael
Waidner
IBM Research, Zurich Research Laboratory
{mts,evh,wmi}@zurich.ibm.com
Abstract:
We have developed some tools for managing policies that are formalized in the
Enterprise Privacy Authorizationg Language (EPAL). These tools illustrate the
usefulness and versatility of EPAL. In this position paper, we present the
automated translation from EPAL to P3P in more detail.
Enterprises begin to actively manage and promote the level of privacy they
offer to their customers.1 The goals are to obtain better publicity, to
limit liabilities, and to comply with regulations. Visible signs of
enterprises' privacy awareness are privacy statements and privacy seals.
Customers can read such privacy promises explaining how collected data will
be used. They can also examine the privacy seals, TRUSTe [10] for example,
certifying that privacy promises exist and are accessible. In April 2002, the
World-Wide Web Consortium (W3C) standardized the Platform for Privacy
Preferences (P3P) specification [4]. P3P enables Web sites to
describe their data collection practices in a machine readable XML format,
which can then be read and displayed by P3P-enabled browser software or other
user agents. Whether or not the data inside the enterprise is used as
promised by a P3P statement depends on the enterprise's actual privacy
practices as defined by the enterprise's chief privacy officer. Up to now,
these practices are not expressed in a machine-readable language that can be
enforced efficiently. To resolve this problem, IBM has proposed the
Enterprise Privacy Authorization Language (EPAL)2 that defines an XML-based
syntax to formulate fine-grained privacy practices for enterprise-internal
enforcement. We have defined the following tools for using and managing EPAL
enterprise privacy policies:
- Semantics
- EPAL has a well-defined formal semantics that defines the meaning of
a privacy policy. This semantics defines what actions are allowed by
whom on what collected data.
- Translation to P3P
- We show how to ensure consistency between practices and promises
through an automatic transformation between privacy practices
formalized using EPAL [1] and privacy
promises formalized using the W3C Platform for Privacy Preferences
(P3P) [4]. This is
done by means of an automated translation [7] that ensures
that privacy promises are kept up-to-date even if privacy practices
change frequently.
- Policy Comparison
- Based on the formal semantics one can define what it means that one
policy is more restrictive than another. This is important for data
exchange where a sending enterprise must verify that the policy of a
business partner that receives personal data is at least as restrictive
as one's own policy.
These tools enable versatile applications of EPAL in an enterprise. In the
long run, we feel that they can serve as a foundation for a policy handling
environment in an enterprise. In the remainder of this position paper, we
will focus on the translation from EPAL to P3P. This is to again emphasize
that EPAL is not meant as a competitor to P3P. Instead, we feell that both
nicely augment each other: While P3P can be used to formalize clear privacy
promises from an enterprise to consumers, EPAL can be used to formalize
fine-grained privacy policies for enterprise-internal enforcement.
We distinghish two types of privacy policies: enterprise-internal privacy
practices and published privacy promises (see Figure 1). Enterprise
privacy practices define how data is collected, processed, and used (see
Figure 1). They are
required to comply with legal regulations. In addition, they need to
implement the privacy goals and business processes of the enterprise.
Enterprise privacy practices can be formalized using EPAL [1] They can be very
fine-grained and can define access rights down to individual employees. As a
consequence, they may change frequently.
Figure 1: Privacy policy types and negotiation
between individuals and the collecting enterprise.
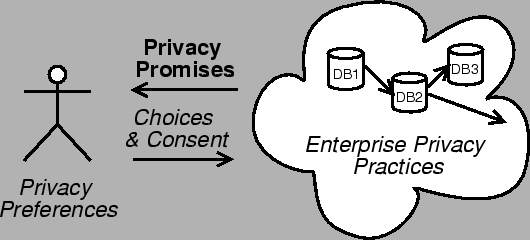 |
Privacy promises communicate certain privacy guarantees to the enterprise's
customer. The most common form are textual privacy statements that explain
what data is collected, how it is used, and what other enterprises may use
it. Compared to enterprise privacy policies, they do not deal with
enterprise-internals but offer a coarser-grained view, considering all the
enterprise-internal data users and the enterprise's business agents as one
data user. Thus, they are quite stable and change only when major revisions
are made. Privacy promises can be formalized using the Platform for
Enterprise Privacy Preferences (P3P) [4]. An enterprise's privacy
practices should be consistent with its privacy promises, i.e., they should
not allow behavior violating a promise. If, for example, an enterprise
promises not to disclose customer addresses to direct marketers, the
practices should ensure that this will not happen. Enterprises also want
privacy promises to properly advertise good privacy practices, i.e., not to
describe data usage or data disclosure that will be prevented by the privacy
practices. If, for example, an enterprise never discloses data to a direct
marketer then it should not ask its customers for permission to do so.
Translating EPAL into P3P
Figure 2: Flows of Enterprise Privacy Policy
Management.
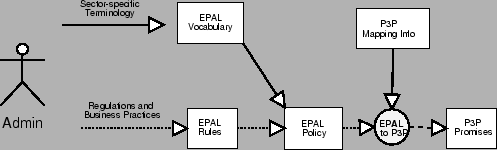 |
The goal of our policy management model is to ensure consistency of published
promises with frequently-changing enterprise-internal privacy practices. This
is done by an automated translation of the enterprise-internal practices,
specified in EPAL, into privacy promises, described in P3P. The flows for
managing policies are depicted in Figure 2, where dotted arrows
denote frequent updates and dashed arrows denote infrequent updates. We now
outline each depicted step in more detail. The enterprise defines its
internal terminology formalized as ``EPAL Definitions'',3. This fixes the scope of the
enterprise privacy practices. In order to enable an automated translation,
this terminology needs to be augmented with P3P specific details that cannot
be derived from the EPAL policy. This is depicted in the box ``P3P Mapping
Info''. The enterprise develops ``EPAL Rules'' that formalize the legal
regulations and the business practices of the enterprise. The ``EPAL
Practices'' result from joining definitions and rules. These formalized
practices are then used as the default policy for using data and enforcing
privacy throughout the enterprise. This can be done using traditional access
control, EPAL-aware business processes, or privacy-enabled access control
systems such as [8]. In order to
derive the corresponding privacy promises, the enterprise uses the mapping
process defined in [7]
to translate ``EPAL Practices'' and ``P3P Mapping Info'' into ``P3P
Promises'' that can be advertised to the customers. Whenever the rules
change, this translation can be re-done to either verify that the changed
rules had no impact on the promises or else to advertise the updated privacy
promises.
The Transformation Procedure Summarized
The complete procedure for transforming a generic EPAL policy to a
corresponding P3P policy consists of following two preparation steps that
need to be done once [7]:
- 1.
- The designer of the transformation defines the P3P data schema to be
used. It may be the base data schema or an enterprise-specific data
schema. The mapping is easier and yields finer-grained results the more
the data sets in the P3P data schema correspond to sub-hierarchies in
the EPAL hierarchy. Re-using the base data schema should result in
better interpretation by some user agents.
- 2.
- The designer of the transformation defines the different mappings.
Each mapping defines a translation of one type of EPAL vocabulary
elements into corresponding elements of P3P.
Whenever a given EPAL policy shall be translated into P3P, this information
is then used in the actual transformation. The transformation consists of the
following steps:
- 1.
- The EPAL policy is translated into a fine-grained EPAL policy.
- 2.
- The fine-grained EPAL policy is transformed into a fine-grained P3P
policy. The general P3P policy information is extracted partially from
the EPAL policy (e.g., contact information), partially from the mapping
tables; and the data schema (or a pointer to it) is inserted. Each of
the fine-grained EPAL rules with a P3P-relevant action and with a
data-user not being the designated data-subject, is translated into a
P3P statement where data group, recipients and purposes correspond to
the P3P labels of the corresponding EPAL elements; and where retention
as well as data, purpose and recipient optionality are determined.
- 3.
- The fine-grained P3P can optionally be aggregated into a
coarser-grained P3P policy. Optionally, an automatic (one statement per
data-element) or semi-automatic (the administrator identifying data to
be grouped in a statement) data aggregation process can aggregate
statements about the same or multiple data elements into one statement.
To avoid ambiguities, the aggregation procedure may
- group statements about the same data by defining unions of its
sub-elements (e.g., the union of two ``optional'' values is their
logical AND; the union of "opt-in" and "opt-out"
is "opt-out"; the union of "opt-out" and "" is
"";
- make statements about parent data types resulting from equal
statements for children;
- group statements about groups of data collected together if so
required, by using the same union mechanisms.
- 4.
- The resulting P3P policy is published on the web-site.
In this position paper, we have sketched tools for handling EPAL policies. We
have elaborated how EPAL policies can be translated into P3P privacy promises
that can be published. This enables up-to-date promises that reflect the
actually enforced privacy policy.
- 1
- P. Ashley, S. Hada, G. Karjoth, C. Powers, M. Schunter (eds.):
Enterprise Privacy Authorization Language (EPAL); IBM Research Report
RZ 3485 (# 93951) 03/03/2003, IBM Zurich Research Laboratory,
Zürich, March 2003.
- 2
- P. Ashley, S. Hada, G. Karjoth, and M. Schunter.
E-P3P privacy policies and privacy authorization.
In ACM Workshop on Privacy in the Electronic Society, pg.
103-109. ACM Press, 2002. .
- 3
- A. Cavoukian and T. J. Hamilton.
The Privacy Payoff: How Successful Businesses build Customer
Trust.
McGraw-Hill Ryerson Lim., 2002.
- 4
- L. Cranor, M. Langheinrich, M. Marchiori, M. Presler-Marshall, and J.
Reagle.
The platform for privacy preferences 1.0 (P3P1.0) specification, Apr.
2002.
W3C Recommendation,
http://www.w3.org/TR/2002/REC-P3P-20020416/.
- 5
- L. F. Cranor.
Web-Privacy with P3P.
O'Reilly & Associates, 2002.
- 6
- S. Fischer-Hübner.
IT-Security and Privacy : Design and Use of Privacy-Enhancing
Security Mechanisms.
Lecture Notes in Computer Science 1958. Springer Verlag, 2001.
- 7
- G. Karjoth, M. Schunter, E. Van Herreweghen: Enterprise Privacy
Practices vs. Privacy Promises - How to Promise What You Can Keep; To
appear in 4th IEEE International Workshop on Policies for
Distributed Systems and Networks (Policy '03), Lake Como, Italy,
June 4-6, 2003.
- 8
- IBM Corporation.
Tivoli SecureWay Privacy Manager Version 3.6.
- 9
- G. Karjoth, M. Schunter, and M. Waidner.
The platform for enterprise privacy practices - privacy-enabled
management of customer data.
In 2nd Workshop on Privacy Enhancing Technologies (PET 2002),
Lecture Notes in Computer Science 2482, pg. 69-84. Springer Verlag,
2003.
- 10
- TRUSTe.
Privacy Certification.
Available at www.truste.com.
Footnotes
-
1
- General introductions to privacy can be found in [3,5,6].
- The pre-decessor of EPAL called Platform for Privacy Preferences
(E-P3P) has been published in [2,9].
- The enterprise may also use a pre-defined terminology or a
terminology that has been standardized in a certain sector.
