Andreas Wagner, Sebastian Speiser, Andreas Harth,
Oliver Raabe, Eva Weis
Karlsruhe Institute of Technology
{first.lastname}@kit.edu
The Smart Grid - a radical redesign of the ageing energy grid - aims at profoundly changing the way how energy is created, distributed and consumed, thereby saving a considerable amount of energy and resources [1,2]. Within the Smart Grid, however, novel challenges arise. Most notably, more information is collected, published and handled by various actors. Data circulating in the grid is highly sensitive, as it is personal information (consider e.g. energy consumption data) and thus must be handled in compliance with existing regulations. In particular privacy laws may be affected and have to be enforced. However, traditional means, i.e. organisational control, for enforcement are not sufficient anymore, due to the high frequency and volume of the data transactions in the grid [3,4]. We argue that a technical enforcement, in addition to organisational means, is needed to ensure compliance with privacy regulations.
Our main contribution in this paper is two-fold: (i) we show how Semantic Web technologies enable a privacy-aware framework for the Smart Grid and (ii) we outline basic privacy principles, enabling a technical privacy enforcement.
The rest of the paper is structured as follows: we describe how privacy and its enforcement may be simplified via privacy principles in Section 2. We introduce our communication and policy model in Section 3. In Section 4 we outline privacy principles we identified, plus describe their realisation in our model. Finally, we conclude with Section 5.
The classic European data protection law is, in contrast to the Anglo-American system, almost completely based on written law. The data protection law describes exactly what is allowed and what is forbidden. However, in complex information systems (e.g. the Smart Grid), data flows are not restricted to a single national system. Flows are rather processed in different locations (with different laws) all over the world. Additionally, due to the rapid technical development, a legal ex-ante control is becoming increasingly difficult [5]. The European data protection rules can thus not change in compliance with technological developments, which hinders innovation. Lastly, a supervision by state authorities will fail completely w.r.t. future systems. A missing enforcement, however, results in a low risk of detecting infringements, thus actors could be tempted to bend the rules.
As a solution, there have been various strategies proposed. One concept is self-regulation, where infringements are not regulated by the legislator, but by the involved parties themselves, in order to resolve conflicting interests [6]. However, self-regulation may fail, if actors do not show enough interest. In summary, due to missing guidelines and sanctions, one might argue that eventually software developers decide on the level and content of data protection.
Given such a background, in Germany the standpoint has been established that data protection regulations need to be simplified. The golden rules of data protection are such an attempt to make current regulations easier [7]. Considering the overlapping aspects of different legal systems, one could argue that there are fundamental congruent views on data protection throughout the world. Such congruent views can be seen as generic law and form a basis for a common legal framework [8].
It is still unclear, however, which (universal) principles should be used as basis for the generic data protection. If an agreement is reached, the current lack of privacy enforcement and control, can be resolved: the basic principles could be transformed in formal, technical rules. Employing automated rules would result in software being able to (in contrast to human actors) enforce privacy directly and completely [9]. Furthermore, any action may be logged and documented. Overall, the privacy deficit could be resolved best via a technical, rule-based enforcement.
However, principles are abstract in their nature. Therefore, in a second step, one needs patterns for concrete rules and strategies for transforming generic principles into concrete rules. Note, w.r.t. behaviour control via rules, the democratic legitimisation of the applied rules is of importance [9]. Thus, it makes sense to select such rules that are best legitimatised. The EU Commission has - in the standard contractual clauses for the transfer of personal data to third countries in Europe (see [10]) - already defined rules, which have (in a broader sense) a democratic legitimisation. Also, with the Safe Harbor Principles, there are further materials available, which can provide guidelines for forming concrete rules.
In summary, via the annexes of the standard contractual clauses in [10], patterns for the modelling of concrete rules may be obtained.
Data produced by the Smart Grid relates to entities that are of interest in various domains. Consider e.g. energy consumption data referring to a specific device, e.g. a washing machine, which again is linked to information on the washing programs used. We assume that devices can host their own linked data endpoints and control the release of their data. Some data is associated with legal requirements, e.g. consumption data (which must be shared with the utility provider for billing purposes). Such data is hosted by a trusted party, i.e. a metering provider.
Our communication model is as follows: data consumers request the data for each usage. A request is accompanied by a statement about the requestor's identity and the usage purpose. The data source (e.g. an appliance or a metering provider) matches the request with an applicable policies p of the data owner (i.e. the energy consumer and appliance owner) to (i) decide if the access is allowed, and (ii) what data should be returned. The matching procedure is implemented as a rule, checking whether (i) the requestor is subsumed by the recipient description in p and (ii) the requested purpose is subsumed by the allowed purpose in p. We assume that the purpose and the recipient/requestor description link to the same trusted (hierarchical) definition. Thus, a subclass-of or same-as check is sufficient for realising the subsume operation.
According to the matching result the corresponding data (or an error code) is returned to the requestor. The data is coupled with a policy specifying the terms of agreement.

Our policy model gives users control over their data by enabling
them to specify their intents in a machine-interpretable manner and
thus allowing them to restrict or permit data access. However,
allowing access to some data does not imply access to all data. We
propose that users are allowed to define various data perspectives. A
perspective is given by a SPARQL query. Using the CONSTRUCT operator
a new graph can be defined depending on the original graph. This means
that triples matching certain criteria, specified in the WHERE and
FILTER clauses can be included or excluded from the original graph.
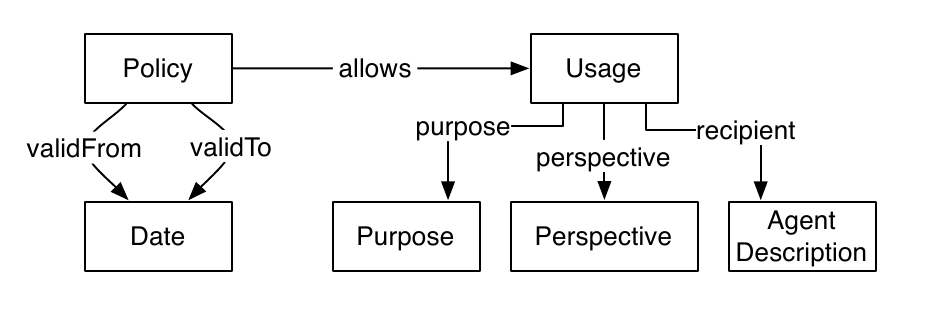
Based on such perspectives we can describe a Policy
with the following attributes: (i) a time span during which it is valid
via validFrom and validTo and (ii) a number
of allowed Usages. An allowed usage is
restricted to a specific purpose, a specific
perspective and can be restricted to a certain recipient.
Note, recipient and purpose link to externally defined concepts. We argue that with respect to purposes, it makes sense to refer to URIs defined by a trusted third-party organisation, which provide useful and reliable definitions for different purposes. Note that this model is comparable to the Creative Commons approach, where e.g. a non-commercial clause is defined that can be referenced by different licenses.
Our approach focuses on the expression of a user's intent (and matching the intent with an incoming request), but could be extended to enforce access control by verifying the requestor's authentication. This could e.g. be realised by requiring that each requestor presents a logical proof of his identity, based on axioms from trusted sources [11].
Using the standard contractual clauses in [10], we identified the following basic privacy principles. Furthermore, below we outline whether each principle may be formalised and, if so, how it is realised via our model.
Liability and third party rights Description: "Each party shall be liable to the other parties for damages it causes by any breach of contractual clauses.", cf. [10]. Formalisable: No. Realisation: N/A. |
Purpose limitation Description: Information has to be used in accordance with the purpose it was originally published for. Formalisable: Yes. Realisation: Our approach supports purpose limitation, as requested data is always released together with a policy describing the intended purpose. Assuming the integrity of the policy, there is no mechanism to modify the original purpose later on. Additionally, one can implement automatic checks for purpose modifications and legitimate usage at each host, thereby enabling a technical enforcement. |
Data quality Description: "Personal data must be accurate and, where necessary, kept up to date.", cf. [10]. Formalisable: Yes. Realisation: Not yet integrated in our approach. However, data quality can be guaranteed via a rule requiring periodical requests for all stored data (i.e. URIs). Thus, data can be updated automatically, in case the new data does not match the old one. |
Data economy Description: "The personal data must be adequate, relevant and not excessive in relation to the purposes for which they are transferred and further processed", cf. [10]. Formalisable: Yes. Realisation: Not yet integrated in our approach. However, e.g. anonymisation of consumption data by means of pseudonyms, would satisfy the data economy principle, while allowing a regular billing process. |
Transparency Description: "Data subjects must be provided with information necessary to ensure fair processing, unless such information has already been given by the data exporter.", cf. [10]. Formalisable: Yes. Realisation: Transparency is fully integrated within our solution, as we assume that for each task the data is requested at its source. With each look-up, the user is notified about the request, its purpose and the recipient. Furthermore, a technical enforcement can be implemented, as data and policies are represented in a machine-interpretable manner. |
Information security Description: "Technical and organisational security measures must be taken by the data controller that are appropriate to the risks, [...].", cf. [10]. Formalisable: No. Realisation: N/A. |
Confidentiality: Description: "Any person acting under the authority of the data controller, including a processor, must not process the data except on instructions from the data controller.", cf. [10]. Formalisable: No. Realisation: N/A. |
User rights (i.e. rights of access, rectification, deletion and objection): Description: "[...] data subjects must [...] be provided with the personal information about them that an organisation holds [...] Data subjects must be able to have the personal information about them rectified, amended, or deleted where it is inaccurate or processed against these principles. [...] A data subject must also be able to object to the processing of the personal data relating to him if there are compelling legitimate grounds relating to his particular situation. [...]", cf. [10]. Formalisable: Yes. Realisation: User access rights are integrated. A user requesting data from a company may link to an "Access personal information"- purpose and a law-based rule can be implemented, granting him access to his data. The remaining rights are not yet supported. However, one could imagine a rule, employing policy modification at host-level to enforce rectification or deletion of incorrect data. |
Sensitive data: Description: "The data importer shall take such additional measures [...] as are necessary to protect such sensitive data [...]", cf. [10]. Formalisable: No. Realisation: N/A. |
In this paper, we have argued that via royalty-free and open standards a privacy-aware Smart Grid can be implemented. We showed how Linked Data principles are applied, leading to a distributed system, where users retain full control over their personal information via policies. We outlined how complicated privacy regulations may be simplified, resulting in nine fundamental principles. Lastly, we described how technical rules for enforcing current privacy regulations may be realised via our privacy principles.
[1] European Technology Platform - SmartGrids Vision and Strategy for
Europe's Electricity Networks of the Future, European Commission, 2006,
http://www.ec.europa.eu/research/energy/pdf/smartgrids_en.pdf.
[2] NIST Framework and Roadmap for Smart Grid Interoperability Standards, Release
1.0. Technical report, National Institute of Standards and Technology, 2010.
[3] Cavoukian, A., Polonetsky, J., and Wolf, C.. SmartPrivacy for the Smart
Grid: embedding privacy into the design of electricity conservation. Identity in the
Information Society, April 2010.
[4] McDaniel, P. and McLaughlin, S.. Security and Privacy Challenges in the
Smart Grid. IEEE Security and Privacy, 7:75–77, 2009.
[5] Ladeur, K.-H.. Datenschutz – vom Abwehrrecht zur planerischen Optimierung
von Wissensnetzwerken: Zur "objektiv-rechtlichen Dimension" des Datenschutzes. DuD - Datenschutz und Datensicherheit 24(1), 2000.
[6] Büllesbach, A.. Selbstregulierung im Datenschutz. Recht der Datenverarbeitung 1/2005, 2005.
[7] Bizer, J.. Sieben Goldene Regeln des DatenschutzesDuD • Datenschutz und Datensicherheit 31 (2007) 5, 2007.
[8] Lutterbeck, B.. VOM «EMPIRISCHEN» ZUM «GENERISCHEN» RECHT Der Beitrag der Institutionenökonomik, 2008.
[9] Orwath, C., Raabe, O. Buchmann E., et al. Software als Institution und ihre Gestaltbarkeit, Informatik Spektrum , 2009.
[10] European Commission, Commission Decision C(2004)5271,
Model Contracts for the transfer of personal data to third countries, 2005
[11] Weitzner, D. J., Hendler, J., Berners-Lee, T. and Connolly, D.. Creating a
Policy-Aware Web : Discretionary , Rule-based Access for the World Wide Web, chapter I, pages 1–31. IRM Press, 2005.