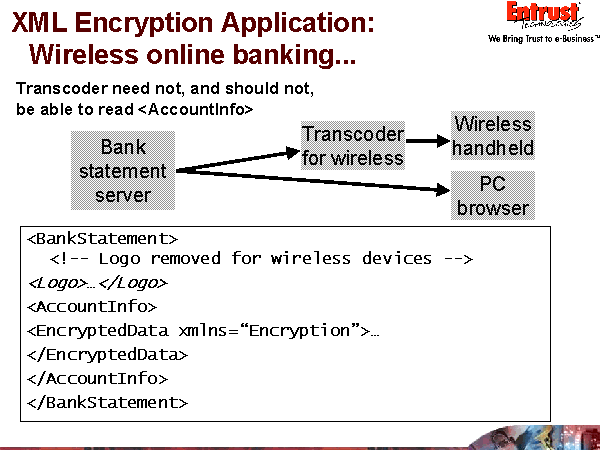
Brokerage wants to provide access to stock trading through handheld device and uses a transcoder to strip out images.
Transcoder needs to be able to parse and filter the XML but should not have access to sensitive data.

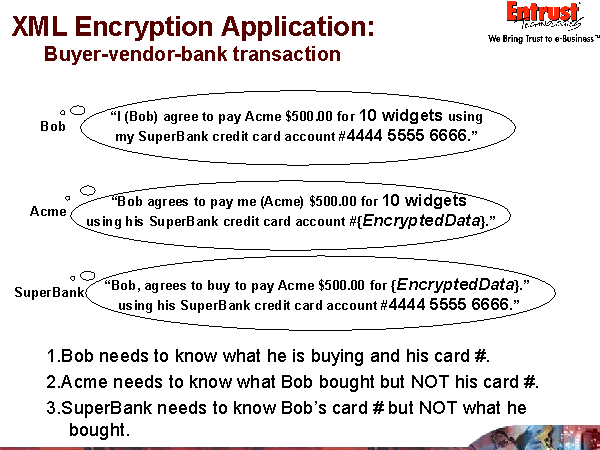
<Invoice>
<Buyer>Bob</Buyer>
<Goods>
<EncryptedData xmlns=“Encryption”> <DecryptionInfo> {Acme’s encryption public key} </DecryptionInfo>
</EncryptedData>
</Goods>
<CreditCard Type=“SuperBank”>
<EncryptedData xmlns=“Encryption”> <DecryptionInfo> {SuperBank’s encryption public key} </DecryptionInfo>
</EncryptedData>
</CreditCard >
</Invoice>
Invoice’s encrypted nodes encrypted for different organizations.
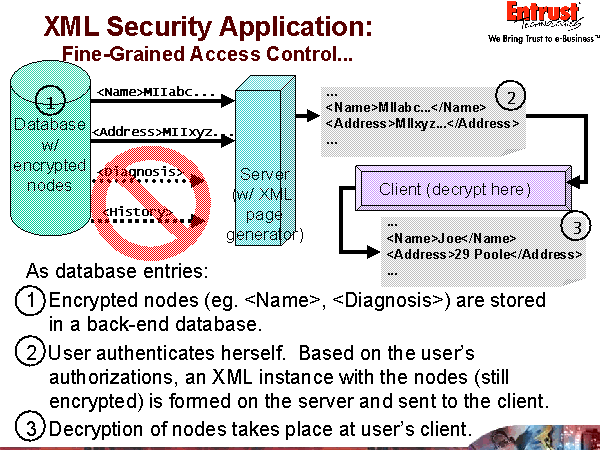
Scenario: A teaching hospital maintains patient records in XML. Each record consists of the patient’s name, address, diagnosis, and history.
Doctors are allowed to see the entire patient record, and update the diagnosis and history.
Administration can see only the patient’s name and address, and only update the address.
Researchers can see only the history and diagnosis. Cannot update any part of the record.
<MedicalRecord>
<Patient SerialNumber=“ {EncryptedAttribute} ”>
<Name> <EncryptedData…> </Name>
<Address> <EncryptedData…> </Address>
<Diagnosis> <EncryptedData…> </Diagnosis>
<History> <EncryptedData…> </History>
</Patient>
</MedicalRecord>
Who can see what:
How XML Security can help:
“XML Encryption will specify an XML-based syntax and processing rules for encrypting both XML nodes and arbitrary data”
XML Encryption has two principal elements:
In the encrypted version of an XML instance, the <> element will appear in place of the non-attribute plaintext node that was encrypted. For example:
Before:
<Element>
<Cat/>
<ElementToBeEncrypted>
<Rabbit/>
</ElementToBeEncrypted>
<Dog/>
</Element>
After:
<Element> <Cat/> <EncryptedData xmlns=“...”>qYrSiO2R5X...</EncryptedData> <Dog/> </Element>
1. Serialize (into a string) the node list to be encrypted.
2. Encrypt the string and put it in a <CipherText> element.
3. Create the <EncryptedData> element, put in the <DecryptionInfo> and
<CipherText> elements.
4. Replace the plaintext node list with the <EncryptedData> element.
1. Find an <EncryptedData> element(s) with Type attribute equal to
“Element” or “ElementContent”.
2. Decrypt the text nodes of the <CipherText> element to form an XML fragment.
3. Parse the XML fragment into a DOM node list.
4. Replace the <EncryptedData> element with the node list.
Because attributes are inside elements, one cannot just pop in an element in place of an attribute.
So, if one or more attributes of an element need to be encrypted, an EncryptedDataManifest attribute pointing to a list of encrypted nodes is added to that element. Here’s how it looks:
< AttributeA="A" AttributeB="B" AttributeValueToBeEncrypted1="ONI9WvqL7RFN9FBB59kC3A==" AttributeValueToBeEncrypted2="A2e35shNcL5sWwUKfyzHoQ==" enc:EncryptedDataManifest="./EncryptedDataManifest" xmlns:enc="http://www.example.org/xmlenc"> < xmlns="http://www.exampleorg/xmlenc"> < Name="AttributeValueToBeEncrypted1” Type="AttributeValue">...</EncryptedData> < Name="AttributeValueToBeEncrypted2” Type="AttributeValue">...</EncryptedData> </EncryptedDataManifest>...</Element>
1. Encrypt the attribute value and replace the attribute’s plaintext value with
ciphertext. Repeat for each attribute value to be encrypted.
2. Add an EncryptedDataManifest attribute to the owner element; give it the xmlenc
namespace .
3. Create an <EncryptedDataManifest> element as a child of the owner element.
4. For each encrypted attribute value, create an <EncryptedData> element specifying
its Name attribute as the name of an attribute whose value was encrypted. Include the
<DecryptionInfo> element with the info for decrypting that attribute.
1. Find an <EncryptedData> element with Type attribute equal to
“Attribute”.
2. Obtain the decryption parameters from the <DecryptionInfo> child.
3. Obtain the name of the encrypted attribute value owner from the <EncryptedData>
Name attribute.
4. Decrypt the encrypted attribute value and set the attribute value as the derived
plaintext .
Some questions:
XML Encryption can encrypt one or more arbitrary data instances.
< xmlns=“http://www.example.org/xmlenc”> < Type=“video/mpeg” Name=“secret.mpg”> <>…</DecryptionInfo> < URI=“http://www.example.com/videos/secret.enc”/> </EncryptedData> < Type=“text” Name=“secret.txt”> <>...</DecryptionInfo> <>...</CipherText> </EncryptedData> </EncryptedDataManifest>
The above example covers two encrypted data sources (say for SMIL): an MPEG video with referenced ciphertext (detached encryption?) and a text file which is encrypted and stored directly in the <> element.
Psuedo-syntax:
<EncryptedData Type=“...” Name=“...”> <DecryptionInfo URI=“...”?>…<DecryptionInfo>? <CipherText URI=“”?>…</CipherText>? </EncryptedData>
Attributes:
Children:
The <DecryptionInfo> element contains information about the decryption key:
<DecryptionInfo (Id=)? (URI=)?> <Method Algorithm=”..."/><!-- The decryption method --> <PropertyList>...</PropertyList> <Manifest>...</Manifest> <!-- Pointers to <EncryptedData> elements --> <KeyInfo> <Value/>? <!-- Raw key value --> <Identifier/>? <!-- Key identifier --> <Agreement/>? <!-- Key agreement data --> <EncryptedKey/>+ <!-- Info for encrypted decryption keys --> </KeyInfo> </DecryptionInfo>
XML Encryption can be data-centric or key-centric: An <EncryptedData> element can indicate the associated <DecryptionInfo> element OR A <DecryptionInfo> element can indicate associated <EncryptedData> elements
XML Encryption works with XML Signature so that data can be signed then encrypted OR encrypted then signed
Signed then Encrypted
On verification of the signature, an XML Signature transform is called to decrypt the data
before the hash is calculated.
Encrypted then Signed
No special processing required.
<></></x> OR <></><> OR <>
Ed Simon Entrust Technologies ph: (613) 247-2583 email: ed.simon@entrust.com
or ejs19630722@hotmail.com