Motivation
- XML is highly structured data
- Goal of encryption is destroying / revealation of data's structure
- These contradictions must brought together by XML Encryption
Server-side Access Control (1)
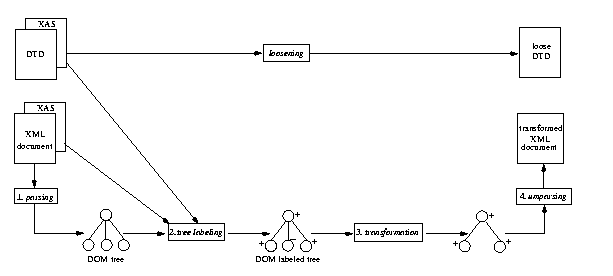
Server-side Access Control (2)
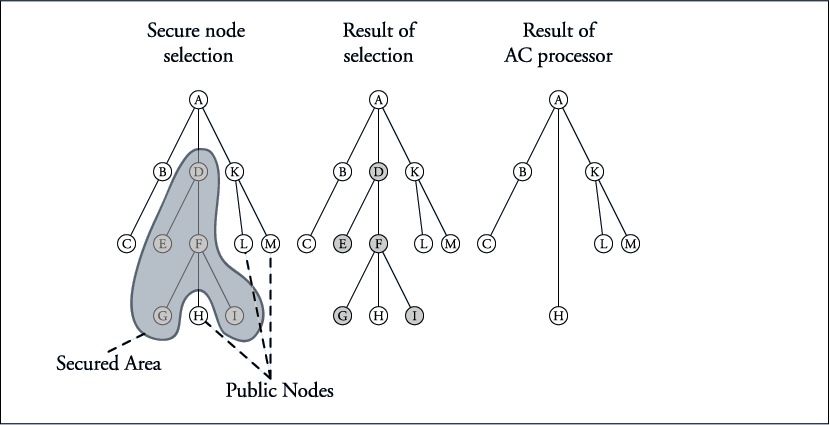
Subtree encryption
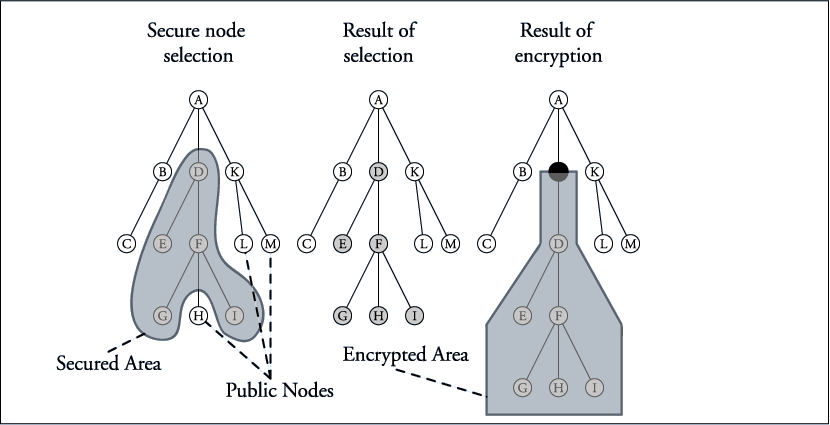
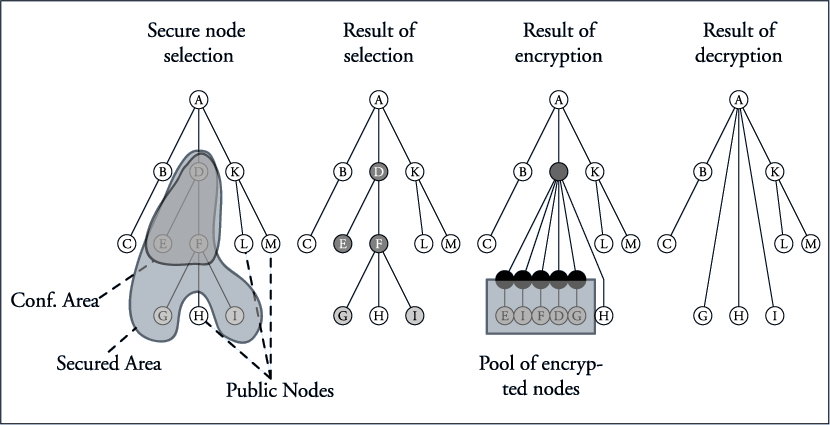
The rough idea of XML pool encryption
- classify the nodes (who can see what?, tree labeling)
- encrypt each node and it‘s position information with an individual content key
- bundle content keys together for each client, depending on 1st step and encrypt the key
information for the clients
- bundle these nodes together with the key information into a new element
Pool Encryption (full access)
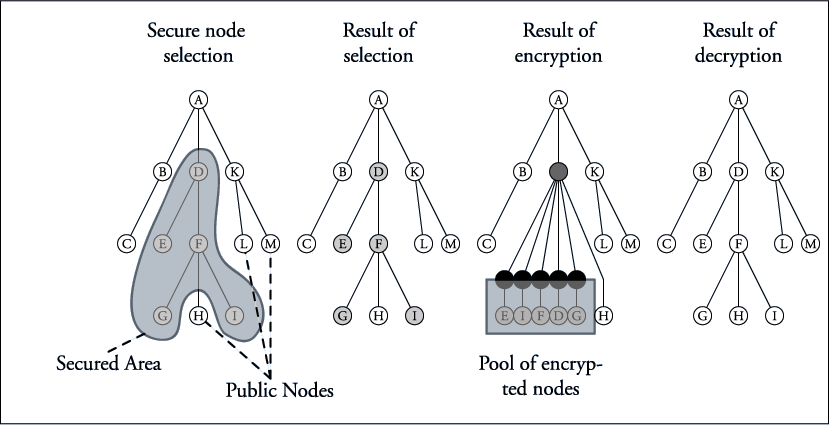
Pool Encryption (restricted access)
Comparison of the approaches
| Model |
Server-Side Access Control |
Subtree encryption |
Pool encryption |
| Secure complete subtrees |
possible |
possible |
possible |
| Secure only attribute values |
possible |
possible (depends on proposal) |
possible |
| Leave "deep" descendants visible |
yes |
no |
yes |
| Needs trustworthy server |
yes |
no |
no |
| Automation of access/encryption decisions |
yes |
needs some sort of style sheet |
needs some sort of style sheet |
| Needs additional transport security (SSL) |
yes |
no |
no |
| New recipients can without reencrypting content |
yes, only new (X)ACL |
depends on situation |
yes |
Properties of pool encryption
- Flexibility of server-side AC is available in a real end-to-end scenario
- Deep public nodes are possible
- Dummy nodes can prevent traffic analysis attacks
- Performance problem: Heavy tree operations will consume memory and computing power
- If the number of client grows and the security requirements are fine-grained, the system
shows it's power
- new clients can be added without modifying encrypted content
01 <?xml version="1.0" encoding="UTF-8"?>
02 <document>
03 <poolEncryption>
04 <encryptedNodes>
05 <encryptedNode id="hukj645" encryptionAlgo="">
06 <base64_and_encrypted_Wrapper>
07 <positionInformation>
08 <anchestors refs="#h566, #763, #8465"/>
09 <precedingSiblings refs="#hd26, #7363, #8dg65"/>
10 </positionInformation>
11 <elementType>Element</elementType>
12 <elementContent></elementContent>
13 <namespaceInfo></namespaceInfo>
14 </base64_and_encrypted_Wrapper>
15 </encryptedNode>
16 </encryptedNodes>
17 <keyMaterial>
18 <clientPackage id="client1" clientId="geuer-pollmann">
19 <packageEncryptionKey Algo="RSA" Encoding="base64">567886439875==</packageEncryptionKey>
20 <keyCollection Algo="AES">
21 <base64_and_encrypted_Wrapper>
22 <keys>
23 <key ref="#hukj645">0x65ffe34a</key>
24 <key ref="#7363">0x0123456</key>
25 </keys>
26 </base64_and_encrypted_Wrapper>
27 </keyCollection>
28 </clientPackage>
29 </keyMaterial>
30 </poolEncryption>
31 </document>





