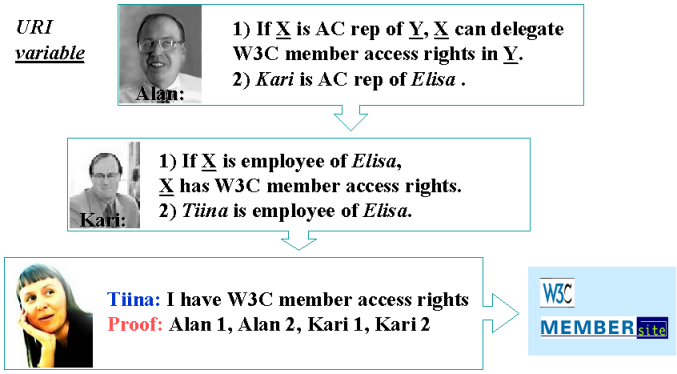
This example was inspired by, and roughly follows, Marja-Ritta's slide

in which access to a member area on the web site is granted to Tiina by authority delegated by Alan, in charge of the web site, to Kari. (This in turn was based on an example in the statement of work for Darpa DAML funding for MIT-LCS Semantic Web work) Public key tools are very flexible, and so one can make all kinds of system. Here is one. The key document is access-rule.n3, which defines the rule for access being allowed to the site. It defines what information is beleived and on what basis.
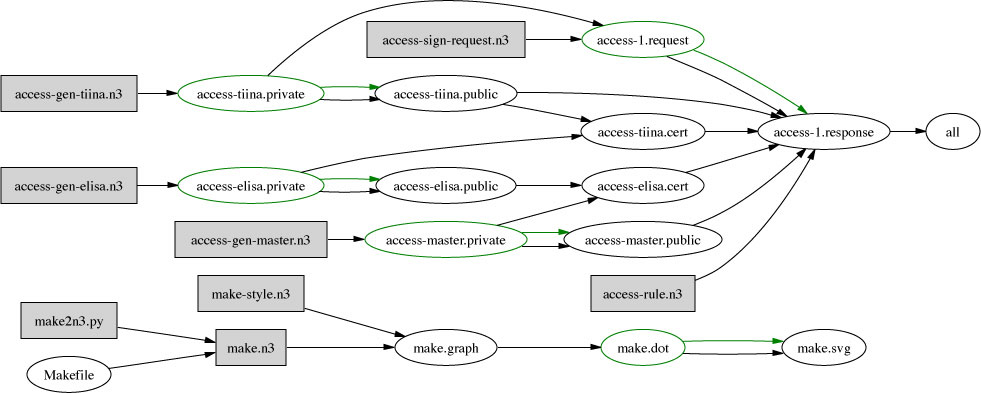
The other files are listed below. The Makefile describes how they used (diagram in SVG). The .n3 file extension is used only for source rule files. Files which are generated automatically are given other extensions, like .private, .public, .cert, .request, .response even though they are still all in n3.
This is a hand-made file. See also up-to-date listings in order of: Name Last modified Size Description
The makefile is the place to start
Parent Directory 14-May-2002 19:59 -
Makefile See how the files are built.
acc.n3 Schema for access control terms
access-1.request The request from a web client
access-1.response The response from this system
access-elisa.cert Elisa corp's certificate, signed by Alan
access-elisa.private Elisa corp's secret file with private and public keys
access-elisa.public Only the public key information
access-gen-elisa.n3 N3 rule file to generate access-elisa.private
access-gen-master.n3 N3 rule file to generate access-master.private
access-gen-tiina.n3 N3 rule file to generate access-tiina.private
access-master.private Master keys held by Alan Kotok
access-master.public public key only of Alan's keys
access-onlyPublic.n3 N3 rules for removing any acc:Secret information
access-rule.n3 The rule defining access to the web site
access-sign-cert.n3 Rule file for signing Tiina's certificate.
access-sign-member-cert.n3 Rule file Alan uses to sign member certificates.
access-sign-request.n3 Rule file Tiina uses to sign the request
access-tiina.cert Tiina's certifiacet as employee of Elisa
access-tiina.private Tiina's private keys - a file she keeps secret
access-tiina.public The publci part of Tiina's key OTHER TESTS of the crypto builtins:
crypto-test-out.n3 What you would expect from crypto-test.n3
crypto-test.n3 A simple first test
hash-data.txt data for test-hash.n3
hash-out.n3 expected output
test-hash.n3 test hashes, does not need public key.
test-n3String.n3 test of a log:n3String function
test-parsedAsN3.n3 test of a log:parsedAsN3 function Myfile.txt 05-May-2002 02:46 1k